Appendix: “Life cycle” of international travel surveillance (longer version)
Voir la page entière pour imprimer SommaireAs mentioned above, the process of screening all people who travel to, from, within, or even over the US begins well before anyone steps into an airport. Surveillance, identification, cross-checking and prediction processes may begin with the click of a mouse on someone’s home computer in a country far away. Here, we detail a longer version of this process than what is included in the report, that includes more extensive descriptions of datasets and systems.
1. If you are a non-citizen, before you can legally enter the US you must apply for a visa and/or have your passport checked.
If you were born in one of the 38 countries that qualify for the US’ visa waiver program, you don’t need a visa for some short-term visits.
If you were born in a country that is not eligible for visa waivers, you must obtain authorization, in the form of a non-immigrant or immigrant visa, from the US Department of State (DOS), issued at an US Embassy or Consulate. Visa applications automatically generate multiple biographic and biometric checks against multiple criminalizing and suspected terrorist databases that seek to verify an applicant’s identity and match them to derogatory information.Note en bas de page 1
Databases used to approve or “vet” visas:
- Electronic System for Travel Authorization (ESTA)
- Consular Consolidated Database (CCD)
The DOS uses its Consular Consolidated Database (CCD) to vet visa applications. CCD is a near real-time aggregate that stores current and archived data from all US consulates around the world.Note en bas de page 2 CCD contains information about US citizens as well as legal permanent residents and foreign nationals who apply for nonimmigrant and immigrant visas. Immigrant and non-immigrant visa application details, including rejected applications with vetting comments, are shared between DHS, the FBI, the Department of Defense, and other federal agencies implicated in the visa and passport review and approval process. Applicant photographs stored in CCD include those from previous passports and visas, and are automatically registered for facial recognition. CCD contains financial, medical, educational information, family relations, international adoption information, arrests and conviction data, race, social media accounts, and information from commercial data brokers and public records.Note en bas de page 3
Additionally, CBP’s National Targeting Center (NTC) “continuously vets” all holders of immigrant and non-immigrant visas of travelers before they board US-bound flights.
NTC checks the following:
- Terrorist Screening Database
- CCD
- INTERPOL wants/ warrants
- US immigration violations
2. As soon as you purchase your airline ticket, your reservation information and itinerary become available to DHS.
This information is stored and retrievable as the following data:
When you buy an airline ticket, a computer reservation system (likely managed by major global distribution systems that handle booking and are contracted by airlines), retains the details of the transaction in the form of a “passenger name record” (PNR, as mentioned above). A PNR number is assigned. This may be called a record locator, booking reference, or reservation code. It is an automatically-generated code with five or six alphanumeric characters. In addition to your full name, timestamped IP address, credit card number, itinerary, and email address, a PNR file may include information about your travel companions.Note en bas de page 4 It could list your emergency contacts, records from transportation other than flights, car rental history, organizational affiliations or employer.Note en bas de page 5 It might archive your hotel reservations (including number of beds requested), records of meal requests, and free-form notes made by officers at national borders.Note en bas de page 6 PNRs are commercial data that are stored in and mined by various DHS tools for patterns to predict “risk” and “identify abnormalities in travel patterns.”Note en bas de page 7
3. Your personal profile and information — your name, ethnicity, national origin, travel itinerary, occupation, personal, political, religious and professional contacts and associations — can be screened by DHS.
Your personal profile and information — your name, ethnicity, national origin, travel itinerary, occupation, personal, political, religious and professional contacts and associations — can be screened by DHS using black-box, rules-based algorithmic predictions as well as matched against various secret watchlists. These secret and changing rules determine whether and how you may be targeted for harassment and arrest once you do show up at the airport.
In November 2001, then-President Bush signed the Aviation and Transportation Security Act into law, creating the Transportation Security Administration (TSA) — a division of DHS that operates a travel-permission system for domestic US flights called “Secure Flight.”
“Secure Flight” began as a program where aircraft operators screened names from passenger reservations to see if they matched or closely resembled any included on a “No Fly List”Note en bas de page 8 and other federal watchlists of “known or suspected terrorists” created by the FBI. If the aircraft operator suspected a watchlist match, the operators were supposed to notify TSA and send the targeted passenger for enhanced in-person screening.
Today, “Secure Flight” allows TSA to access CBP’s surveillance dragnet and prediction tool — Automated Targeting System, or ATS, (more on this below) and write rules for the algorithm used by the ATS system to decide who qualifies as a “risk” and will be added to a category of people who will be subject to increased security checks. Targeting rules, and therefore the people targeted, can change day to day.Note en bas de page 9
According to a 2019 PIA on ATS: “These rules are based on risk factors presented by a given flight and passenger, the level of screening for a passenger that may change from flight to flight. Travelers may match a TSA or CBP-created rule based upon travel patterns matching intelligence regarding terrorist travel; upon submitting passenger information matching the information used by a partially-identified terrorist; or upon submitting passenger information matching the information used by a Known or Suspected Terrorist.”Note en bas de page 10
Data systems you are screened against and processed by may include:
- Secure Flight
- Various FBI “no fly lists,” including “known or suspected terrorists”
- Automated Targeting System (ATS): more below
- ICM/ TECS
TECS, CBP’s international entry/ exit log of crossings of US borders, is now being “modernized” into Palantir’s ICM. As detailed above, ICM is an “intelligence system” that allows users to access different criminalizing databases and biometric databases — both government-owned and private.Note en bas de page 11 Since 1987, TECS has recorded law enforcement “lookouts,” border screening data, and reporting from CBP’s primary and secondary inspection processes. CBP officers have used TECS as their main system at the border and elsewhere to screen arriving travelers and determine their admissibility.
Buying an airline ticket for an international flight creates a flag in the TECS system if you are already being tracked in the database.Note en bas de page 12 ICE analysts can sign up for notification alerts, so if you have a final order of removal, for example, and purchase an international airline ticket in your name, ICE can send agents to meet you at the airport.Note en bas de page 13
TECS:
- Includes information from the FBI Terrorist Screening Center’s Terrorist Screening DatabaseNote en bas de page 14
- Provides access to NCICNote en bas de page 15
- Connects to NletsNote en bas de page 16
- Includes free-form notes written by CBP officers and Border Patrol agents about individuals with whom they interact. CBP officers and Border Patrol agents can allege that someone’s behavior might be related to intelligence gathering or preoperational planning related to terrorism, criminal, or other illicit intention; this notation will stay on a person’s permanent record, regardless of the outcome of the encounter.Note en bas de page 17
Source: US Government Accountability Office
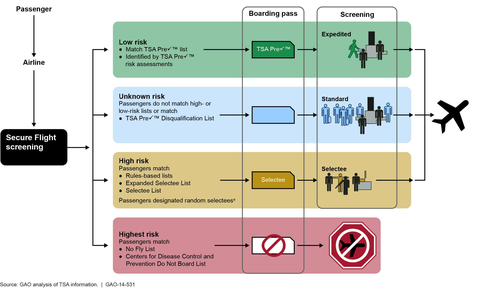
This flow chart describes the following risk levels: low risk (match with TSA pre-check list or identified by TSA pre-check risk assessments), unknown risk (passengers who do not match high or low risk lists or match the TSA pre-check disqualification list), high risk (passengers matching the rules-based lists, expanded selectee list, selectee list, or passengers designated as random selectees), and highest risk (passengers matching the no fly list, or the Centers for Disease Control and Prevention Do Not Board List). The graphic indicates that low risk passengers get expedited screening, unknown risk passengers get standard screening, high risk passengers have their luggage searched and receive a physical pat-down, and highest risk passengers are barred from flying.
4. Once you are inside the airport, your face is overtly and covertly captured for facial recognition and real-time tracking.
CBP uses its own in-house facial recognition matching technology, the Traveler Verification Service (TVS), for identity verification and biometric entry and exit “vetting checks.”Note en bas de page 18
When the traveler enters or exits an airport, border crossing, or seaport, they will pass a camera connected to CBP’s cloud-based TVS facial matching service. The camera may be owned by CBP, the air or vessel carrier, another government agency (like TSA), or an international partner.Note en bas de page 19 If the camera is CBP-owned and operated, a CBP officer will be present. However, if the camera is airline-operated, it may not necessarily be visible. It may be located on a jetway after a passenger scans their boarding pass, and the passenger might not even know an image of their face is being captured. TVS matches the live image of the traveler on the jetway with existing photos in a “gallery” (maintained in IDENT) that archives photographs from CBP’s ATS-UPAX database that might be from previous exits and entries, US passports and visas, from DHS apprehensions, enforcement actions, or other immigration-related records.
5. CBP must approve every single passenger before an international flight departs, arrives in, or overflies the US.
When you check in for an international flight to, from, or that overflies the US, the Advance Passenger Information System (APIS) transmits your PNR data and itinerary (including flight status updates) to CBP. Before you are permitted to board the plane, passport or ID is scanned by a CBP officer or TSA agent. The machine readable zone of their document pulls up your full name, date of birth, and citizenship, which can be used to retrieve information about your scheduled flight. This data is sent to CBP via APIS in the form of “passenger manifests” — commercial airline records that are transferred to CBP for vetting in real-time, or 30 minutes prior to boarding.Note en bas de page 20 APIS generates a “Overstay Lead” list that is shared with CBP’s main computer system that assesses “risk,” ATS.Note en bas de page 21
- 1 a Testimony Before the U.S. House of Representatives Committee on Homeland Security on “Supporting a Fact-Based Approach to Preventing Terrorist Travel to the United States”, 2019, 3 (Donald Conroy, Director, National Targeting Center — Passenger Operations, U.S. Customs and Border Protection, and Monte B. Hawkins, Director, National Vetting Center, U.S. Customs and Border Protection) https://homeland.house.gov/imo/media/doc/Jt.Testimony-Conroy-Hawkins.pdf.
- 2 a U.S. Department of State, “Privacy Impact Assessment: Consular Consolidated Database (CCD),” https://www.state.gov/wp-content/uploads/2019/05/Consular-Consolidated-….
- 3 a “Privacy Impact Assessment: CCD,” 10.
- 4 a “What Is PNR: Passenger Name Record Explained in Details,” Medium, May 13, 2021, https://altexsoft.medium.com/what-is-pnr-passenger-name-record-explaine….
- 5 a Ban Keat Kwa, Dave Hubbard, and Monica Smith, The Value of a PNR Data Warehouse, 2004, https://assets.teradata.com/resourceCenter/downloads/WhitePapers/eb2640….
- 6 a Edward Hasbrouck, “What's in a Passenger Name Record (PNR)?” The Identity Project, accessed July 9, 2021, https://hasbrouck.org/articles/PNR.html.
- 7 a U.S. Department of Homeland Security Privacy Office, Re: DHS/OS/PRIV 07-160/Sobel request, letter, Washington, D.C., from Electronic Freedom Frontier, https://www.eff.org/files/filenode/foia_ats/20071107_ats01.pdf.
- 8 a U.S. Department of Homeland Security, “Privacy Impact Assessment for the Secure Flight Program,” August 9, 2007, https://www.dhs.gov/sites/default/files/publications/privacy_pia_tsa_se….
- 9 a U.S. Department of Homeland Security, “Privacy Impact Assessment for Secure Flight Silent Partner and Quiet Skies DHS/TSA/PIA-018(i),” April 19, 2019, https://www.dhs.gov/sites/default/files/publications/pia-tsa-spqs018i-a….
- 10 a “PIA for Secure Flight Silent Partner and Quiet Skies DHS/TSA/PIA-018(i).”
- 11 a Spencer Woodman, “Palantir Provides the Engine for Donald Trump's Deportation Machine,” The Intercept, March 2, 2017, https://theintercept.com/2017/03/02/palantir-provides-the-engine-for-do….
- 12 a Brian Hauss, “Documents Shed Light on Border Laptop Searches,” ACLU Speech, Privacy, and Technology Project, June 9, 2013, https://www.aclu.org/blog/national-security/privacy-and-surveillance/do….
- 13 a Edward Hasbrouck, “How airline reservations are used to target illegal searches,” The Identity Project, September 17, 2013, https://papersplease.org/wp/2013/09/17/how-airline-reservations-are-use….
- 14 a Privacy Office, Department of Homeland Security, “Notice of Privacy Act System of Records: Department of Homeland Security/ALL-030 Use of the Terrorist Screening Database System of Records,” Federal Register, April 6, 2016, https://www.federalregister.gov/documents/2016/04/06/2016-07895/privacy….
- 15 a Mary Ellen Callahan, “Privacy Impact Assessment for the TECS System: CBP Primary and Secondary Processing,” Department of Homeland Security website, December 22, 2010, https://www.dhs.gov/sites/default/files/publications/privacy-pia-cbp-te….
- 16 a Callahan, “PIA for the TECS System: CBP Primary and Secondary Processing,” DHS, 2010.
- 17 a U.S. Department of Homeland Security, “Privacy Impact Assessment Update for the TECS System: CBP Primary and Secondary Processing (TECS) National SAR Initiative DHS/CBP/PIA-009(a),” Department of Homeland Security website (Department of Homeland Security, August 5, 2011), https://www.dhs.gov/sites/default/files/publications/privacy-pia-cbp-te….
- 18 a U.S. Department of Homeland Security, “DHS/CBP/PIA-056 Traveler Verification Service,” https://www.dhs.gov/publication/dhscbppia-056-traveler-verification-ser….
- 19 a U.S. Department of Homeland Security, “Privacy Impact Assessment for the Traveler Verification Service DHS/CBP/PIA-056,” November 14, 2018, 6, https://www.dhs.gov/sites/default/files/publications/privacy-pia-cbp056….
- Revenir au texte à partir de la note en bas de page 20U.S. Department of Homeland Security, “Privacy Impact Assessment for the Advance Passenger Information System (APIS): Voluntary Expansion DHS Reference No. DHS/CBP/PIA-001(i),” February 10, 2021, https://www.dhs.gov/sites/default/files/publications/privacy-pia-cbp001….
- Revenir au texte à partir de la note en bas de page 21U.S. Department of Homeland Security, “Fiscal Year 2019 Entry/Exit Overstay Report,” March 30, 2020, 9, https://www.dhs.gov/sites/default/files/publications/20_0513_fy19-entry….