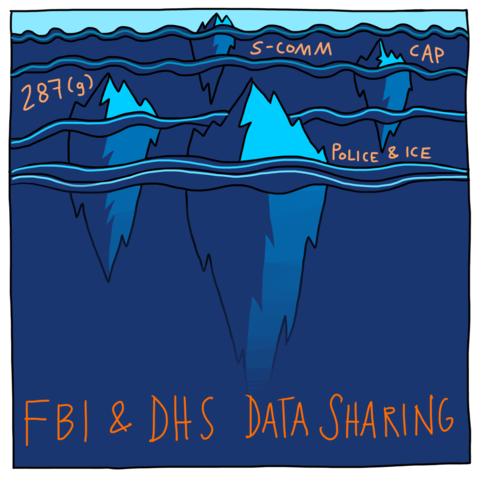
FBI & DHS Data Sharing, S-Comm, 287(g), CAP, Police and ICE
In the following sections, we examine how data criminalization operates within:
- Police encounters and profiling
- Automated data-sharing systems used by law enforcement agencies
- Surveillance capitalism: the expanding market of data brokers, cell phone apps, social media and digital stalking
- Biometric technologies and covert identification practices
- Traveler surveillance and securitization
- Bureaucratic pathways to visas and naturalization
For this report, we do not aim to provide a complete taxonomy of all government and commercial databases used to criminalize, but instead ask how the tangled and blurry morass that we can discern might indicate how a larger machinery operates.
Constructing crimmigration
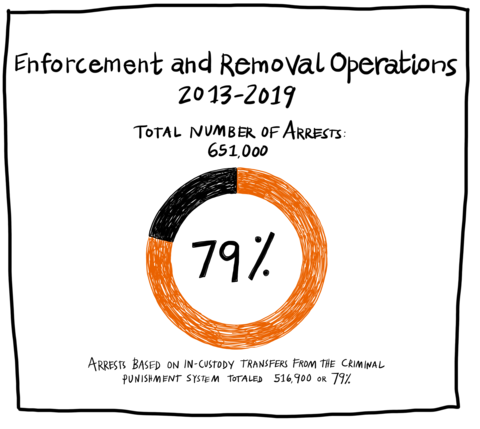
Collaborations and data-sharing between law enforcement and ICE have been the most efficient way to criminalize and deport record numbers of immigrants from the US. The majority of ICE arrests are based on hand-offs from jails and prisons directly to ICE. A 2020 DHS Office of the General Inspector audit analyzed Enforcement and Removal Operations (ERO) data from 2013-2019 and found that “516,900, or 79 percent of its 651,000 total arrests, were based on in-custody transfers from the criminal-justice system.”Note en bas de page 1
Image Source Note en bas de page 2
Enforcement and Removal Operations 2013-2019, Total Number of Arrests 651,000, Arrests based on in-custody transfers from the criminal punishment system totaled 516,900 or 79%
Digitization and centralization of government databases began as early as 1967 with FBI records.Note en bas de page 3 However, the digitization of migrant records came much later. It was not until 2008 that fingerprints accompanying applications for immigration “benefits” like travel visas and naturalization were uploaded, and 2010 when ICE investigators began consistently uploading fingerprints taken from people during law enforcement encounters.Note en bas de page 4
The legal architecture of modern US immigrant criminalization is less than forty years old.
Many key laws have roots as recent as the 1980s, when the Cold War and the racialized War on Drugs collided. In 1986, the Immigration Reform and Control Act (IRCA) criminalized hiring undocumented workers for the first time in US history, and increased resources for the INS to patrol the border.Note en bas de page 5 IRCA also mandated the US Attorney General to deport noncitizens convicted of “removable offenses” as quickly as possible. This began the practice of targeting immigrants convicted of crimes and expanded the mechanisms for policing immigrants.
Source Note en bas de page 6
Modern Legal Architecture of Migrant Criminalization. 1986: Anti-Drug Abuse Act: Set the groundwork for use of detainers. Immigration Reform and Contral Act: Criminalized hiring undocumented workers, More funding for border enforcement. 1988: Anti-Drug Abuse Act: Introduced the aggravated felony concept, denied judicial discrection for release. If Aggravated Felony, Mandatory Detention. 1990: Immigraton Act of 1990: Expanded grounds for removal making it easier to target people for state drug convictions. 1994: Violent Crime Control and Law Enforcement Act: Creates the state criminal aliens assistance program which reimburses local governments for arresting and detaining undocumented immigrants.1996: Anti-Terrorism and Effective Death Penalty Act: Expanded mandatory detention including LPRs, Illegal Immigration Reform and Immigrant Responsibility Act, More people subject to Mandatory Detention, 287(g) Agreements Created.
The Clinton administration continued and expanded those practices, passing the Antiterrorism and Effective Death Penalty Act of 1996, or AEDPA, which created and expanded the grounds for mandatory immigrant detention and deportation, including for long-term legal residents. It was the first US law to formally authorize fast-track deportation procedures, a modified form of which is widely used today.Note en bas de page 7
Additionally, the Clinton administration passed the Illegal Immigration Reform and Immigration Responsibility Act (IIRIRA) in 1996, which conflated immigration and criminality.Note en bas de page 8 IIRIRA is a keystone of our current immigration policy. It:
- enabled the creation of the 287(g) program, which allowed DHS to enter into agreements with local law enforcement to perform certain functions of immigration agents;
- expanded the list of convictions that trigger “mandatory” detention; and
- increased the number of convictions that trigger deportation by further expanding a category applicable only to immigrants that was created by the Anti-Drug Abuse Act of 1988: “aggravated felonies.”Note en bas de page 9
Congress determines which offenses qualify as aggravated felonies (not all aggravated felonies are felonies), and an aggravated felony conviction precludes access to relief like asylum and increases vulnerability to deportation.
Police + ICE collaboration
In the following section, we look at three notable police-ICE partnerships that institutionalized data criminalization of migrants and non-citizens within non-immigration law enforcement protocols.Note en bas de page 10 As we will see, systemic information-sharing at the data network level nullifies many of the sanctuary agreements that are in place today.
Formal FBI and DHS database integration is even newer than the crimmigration laws named above, dating back to around 1998. It accelerated following the 2001 Patriot Act, when Congress mandated the creation of an electronic system to share law enforcement and intelligence information to confirm the identities of people applying for United States visas.Note en bas de page 11 At the same time, Congress restructured federal law enforcement laws to conflate “national security,” “crime control,” and “immigration control.”Note en bas de page 12 Just one year later, in 2002, Congress created DHS and granted it immediate access to information in federal law enforcement agencies’ databases, sealing the deal for an interlocking web of automated database sharing.
Various programs since the 1980s had already given immigration authorities access to police data, jails and prisons. These programs often do not have clear beginning and end dates. There are implementation differences based on region, and there are overlaps and inconsistencies. Furthermore, in response to public pressure opposing formal law enforcement collaborations with ICE, the agency continued its information-sharing collaborations with local and state law enforcement — but often under the radar. Today, much data-sharing and immigration status-querying is built into the computer systems used by law enforcement to perform routine functions (like uploading someone’s fingerprints). Under the current automated systems, every single person who was born outside of the US — or whose birthplace is unknown to US government databases — is automatically scrutinized for deportation if they are arrested and booked for anything, regardless of the charge and whether it is ultimately dismissed.Note en bas de page 13
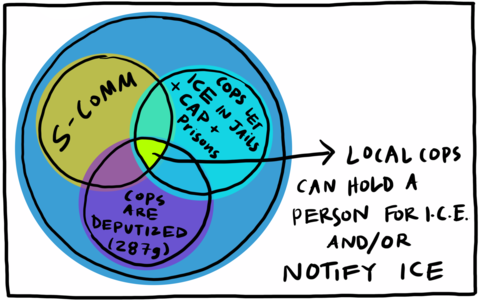
S-COMM, Cops Let ICE in jails and CAP and Prisons, Cops are Deputized 287(g), Local Cops can hold a person for ICE and/or Notify ICE
Criminal Alien Program
The Criminal Alien Program (CAP) has been around in one form or another since a 1986 law decreed that people convicted of certain crimes should be an enforcement priority. CAP has been more aggressive in some states than others. “The unevenness in the program certainly implies that the preferences of state and local law enforcement officers (as well as the preferences of ICE agents in one region or another) played a role,” a Vox article stated.Note en bas de page 14 Today, CAP is an umbrella program that includes a variety of local law enforcement and ICE partnerships with names like VCAS, LEAR, REPAT, DEPORT, JCART, which use tactics ranging from in-person “jail checks” to automated biometric database-sharing.Note en bas de page 15
CAP began as mostly low-tech, voluntary collaborations between local law enforcement and immigration enforcement. Under CAP, jails and prisons often shared booking records with immigration agents and/or allowed immigration agents in-person access to interrogate incarcerated people ICE suspected it could deport — regardless of whether the booked person could eventually be charged or convicted.Note en bas de page 16 CAP allows local cops to funnel people directly into ICE’s custody, and allows ICE to use the criminalization process as a tool to facilitate mass deportations. CAP absolutely is premised on racial and national origin profiling and targeting: If you are a “suspected noncitizen,” that is enough to qualify you for a CAP screening and ICE interrogation in jail or prison.Note en bas de page 17 A 2013 American Immigration Council report found that CAP screens “all self-proclaimed foreign-born nationals found within Bureau of Prisons (BOP) facilities and all state correctional institutions.”Note en bas de page 18
Despite its name, CAP programs were used to deport more than 22,000 immigrants without criminal records between FY 2013 and FY 2016.Note en bas de page 19
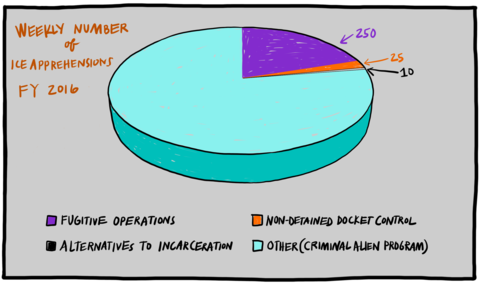
CAP was in place long before S-Comm was piloted in 2008 (more on S-Comm below). It operates out of all ICE field offices, in all state and federal prisons, and many local jails.Note en bas de page 20 It has blended seamlessly with S-Comm machinery and processes, as ICE makes use of many of the same automated database checks set in motion by law enforcement booking and heavily relies on cooperation from jails and prisons to honor detainers and requests for notification of release. During the Obama era, CAP was the primary mechanism through which ICE deported people from the US interior.Note en bas de page 21 Vox reported that CAP was responsible for between two-thirds and three-quarters of deportations during the Obama era of the early 2010s.Note en bas de page 22 TRAC at Syracuse University concluded similarly for FY 2016, based on analysis of case-by-case records on both apprehensions and removals data obtained from ICE in response to hundreds of Freedom of Information Act requests, appeals, and a successful lawsuit.Note en bas de page 23
Source Note en bas de page 24
Weekly Number of Ice Apprehensions FY 2016, Fugitive Operations, Alternatives to Incarceration, Non-Detained Docket Control, Other (Criminal Alien Program)
Although CAP is still known by many as a “jail status screening” program, both CAP and S-Comm use automated systems (detailed below) that attempt to match to FBI files and immigration records biographical and biometric information taken from a person by a cop during booking. Historically, “biometrics” has generally meant fingerprints; today, ICE and the FBI are outfitted with facial recognition software and readily available photo data from state driver’s licenses, visa and naturalization records as well as photos scraped from the Internet and social media.
287(g) agreements
Section 287(g) of the Immigration and Nationality Act (INA) allows DHS to deputize state and local police to carry out federal immigration enforcement through interrogations and arrests, or following resolution of local, state, or federal charges. These partnerships today take two main forms: the “jail enforcement model,” which authorizes local police to issue immigration detainers, or the “warrant service officer model,” which ask jails or prisons to notify ICE, or hold a person for ICE, if a person is suspected of being deportable.Note en bas de page 25 287(g) partnerships are voluntary and formalized through MOU agreements made between state or local law enforcement with federal immigration authorities.Note en bas de page 26
The Trump administration dramatically increased the number of 287(g) agreements — from 34 at the end of 2016 to 151 as of November 2020. However, despite the increase in 287(g) agreements, it is difficult to calculate if deportations increased as a result. ICE claims that it does not break out 287(g) data to count deportations, and instead issues monthly reports of “encounters” that only include “a sampling” of people identified under the 287(g) program.Note en bas de page 27
Secure Communities (S-Comm)
S-Comm was piloted by DHS in 2008. It formalized the now-ubiquitous automated process of forwarding fingerprints collected during law enforcement booking to check against immigration and travel databases for potential deportability.
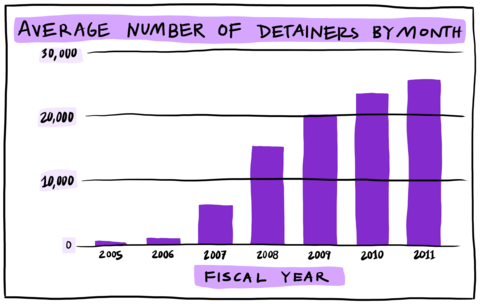
Automating database checks had immediate and dramatic consequences. One product of ICE automation is the detainer (detailed below) — which has taken either the form of ICE requesting that a jail or prison “hold” a person who could be released, or a request from ICE for “notification of release” of a person whom ICE thinks might be deportable. In FY 2005, ICE issued roughly 600 detainers based on automated fingerprint matches per month — but by the end of FY 2011, monthly detainers exceeded 26,000. Although S-Comm was voluntary at first, following opposition from advocates and community members in New York, Massachusetts, and Illinois, the federal government mandated the program.Note en bas de page 28 By January 22, 2013, S-Comm database sharing had been fully implemented in all 3,181 jurisdictions within 50 states, the District of Columbia, and five US territories.
SourceNote en bas de page 29
Average Number of Detainers by Month, Fiscal Year
S-Comm generated much public backlash, and various communities have pressured their jurisdictions and Sheriffs to refuse to cooperate with ICE detainers. TRAC reported that “law enforcement agencies with the most recent recorded refusals were concentrated in New York and California,” and two out of three detainer requests addressed to Queens and Brooklyn Central Booking were recorded as refused.Note en bas de page 30 Santa Clara County in California refused to honor detainers over 90 percent of the time.
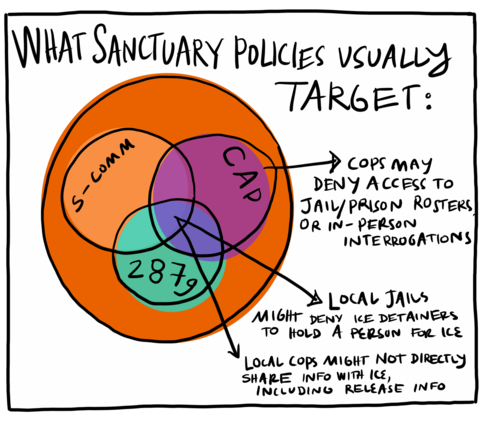
S-COMM, CAP, 287g, WHAT SANCTUARY POLICIES USUALLY TARGET: Cops may deny access to jail/prison rosters or in-person interrogations, Local jails might deny ICE detainers to hold a person for ICE, Local cops might not directly share info with ICE, including release info
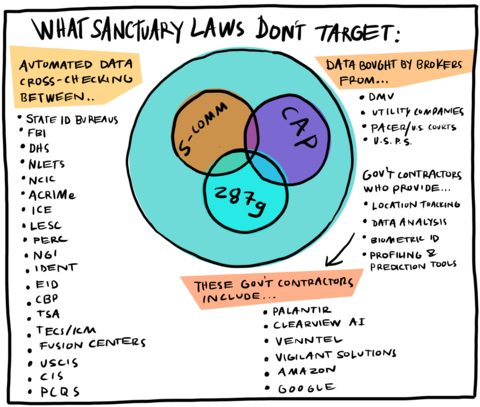
WHAT SANCTUARY LAWS DONT TARGET: AUTOMATED CROSS CHECKING BETWEEN... State ID Bureaus, FBI, DHS, NLETS, NCIC, ACRIMe, ICE, LESC, PERC, NGI, IDENT, EID, CBP, TSA, TECS/ICM, FUSION CENTERS, USCIS, CIS, PCQS; DATA BOUGHT BY BROKERS: DMV, UTILITY COMPANIES, PACERS, U.S. COURTS, USPS; GOV'T CONTRACTORS WHO PROVIDE... Location Tracking, Data Analysis, Biometric ID, Profiling and Prediction Tools, THESE GOV'T CONTRACTORS INCLUDE... PALANTIR, CLEARVIEW AI, VENNTEL, VIGILANT SOLUTIONS, AMAZON, GOOGLE
Laudable though these victories have been for organizers, especially at the local level, it is important to keep in mind that detainers are just the tips of those icebergs — and if a person is not directly transferred to ICE custody from local law enforcement, there are still a number of ways that ICE is able to locate and control a person who is marked by criminalizing databases.
Automated processes of data criminalization
Constant Surveillance and Prediction, "migrant and traveler stalking," "commercial datasets," "arrest + booking," and "HSI and ICE data centers"
How can we dismantle the entire system of data criminalization, which is fully automated at the database and computer level? Here, we take an in-depth look at two of these processes and data systems.
- Arrest and booking: Database cross-checking with some DHS records became standard procedure in daily policing during the era of S-Comm implementation, but things didn’t stop there. Today, criminal punishment data is merged with an expanding array of DHS datasets and commercially sold cell phone app, location and identification data for prediction and profiling purposes. Below, we detail a shortened version of this process, step-by-step.
- Travel surveillance and criminalization: Well before S-Comm, and even before September 11, 2001, airline surveillance and Internet purchase spying was already a norm. Since 9/11, as we will see, the state has largely replaced its former “blacklist” model with algorithmic continuous trolling, creating and using AI to process massive amounts of data and to selectively target any chosen population. Section 7 describes historical and cutting-edge tools and techniques used to covertly identify people in public spaces as well as carceral ones, and match them to multiple private and public datasets in order to evaluate them for the ambiguous quality of “risk.”
Detainers: criminalizing potential
For those of us who are in contact with the immigration system, a detainerNote en bas de page 31 or immigration hold (a version of Form I-247Note en bas de page 32 ) may be the first artifact we encounter in ICE’s data criminalization process that follows a police stop. Detainers are requests by ICE for law enforcement to hold someone in jail or prison for up to 48 hours past the point when they would be released from custody, or to notify ICE prior to release. Some version of an immigration detainer has been used by the precursor to ICE, the INS, since at least the 1950s.Note en bas de page 33 But it wasn’t until S-Comm’s launch in 2008 that issuance of immigration detainers skyrocketed.Note en bas de page 34 S-Comm automated the process, which, combined with the massive legal machinery of immigrant criminalization and deportation that developed over decades, created the data criminalization dragnet that is in effect today.
Detainers cast a wide net, translating ICE’s internal version of “probable cause” into an arrest and possible deportation by attempting to connect the biometric and data profile of a person to records kept by government agencies and commercial databases that show possibility of a visa overstay, entry without inspection, an open warrant, criminal conviction, previous deportation or any other factor that makes a person vulnerable to ICE arrest.Note en bas de page 35
For much of the last decade, ICE has relied heavily — ideologically and practically — on the detainer. In turn, the detainer relies on digital automated data cross-referencing. As an October 2020 Congressional Research Service report notes, “most ICE detainers are based on electronic database checks.”Note en bas de page 36
Using the detainer, ICE converts criminalized data into enforcement potential. By merging criminal and immigrant datasets, detainers purport to make real the longstanding claim that immigration is synonymous with criminality, and therefore, immigration and criminal enforcement are the same. But immigration detainers are not legally enforceable judicial warrants or official court “notices to appear;” they are just (legally questionable) requests from ICE to fellow law enforcement.Note en bas de page 37
Not just deportation, but “interoperability” and constant tracking
Detainers are not an endgame in and of themselves. They are visible iceberg tips that are part of automated processes that come downstream following multiple steps of data criminalization.
If we look at detainers alone, the story seems inconclusive. As noted earlier, in FY 2019 ICE did not take into custody up to 80 percent of the individuals for whom PERC issued immigration detainers.Note en bas de page 38 These folks may still be located by ICE at their homes or upcoming criminal court dates for interrogation and/or arrest, but if they aren’t, they may remain in limbo until a new event or encounter triggers the machinery of data criminalization once again.
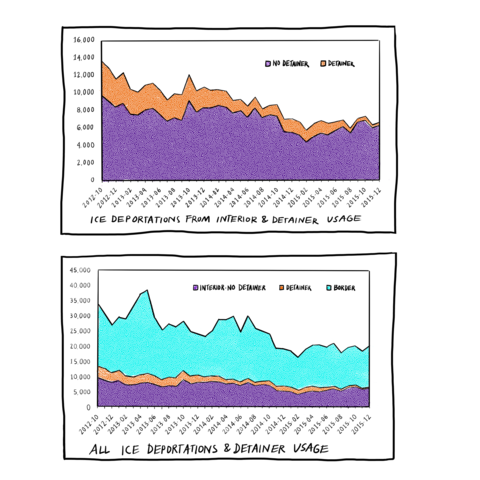
Even amid peak deportations during the Obama era in 2013, S-Comm’s fingerprint match-to-deportation ratio was at its highest, yet accounted for only around a quarter (28 percent) of ICE removals from non-border areas of the US, and less than 12 percent of all ICE removals.Note en bas de page 39 Likewise, despite aggressive support for S-Comm by ICE under Trump, between 2016 and July 2017, only 2.5 to 5 percent of S-Comm deportations from the interior US were the result of detainers sent to local law enforcement agencies. TRAC noted: “When compared with ICE removals from all sources” — not just S-Comm fingerprint matches — “this component made up even a smaller proportion — less than 1 percent of all ICE removals.”Note en bas de page 40
Source Note en bas de page 41
ICE DEPORTATIONS FROM INTERIOR AND DETAINER USAGE, NO DETAINER, DETAINER, INTERIOR-NO DETAINER, DETAINER, BORDER, ALL ICE DEPORTATIONS AND DETAINER USAGE
What the data suggest then is that detainers are not particularly effective as direct pipelines for the deportation of individuals, even those made vulnerable by the criminal legal system. It seems rather that the state’s long game has been to establish a well-oiled “interoperable” machinery of databases that ensure that no matter who is in charge formally, a separate system — governed by targeting decisions, algorithms, and operating procedures — is able to expand and toggle between hidden, real-time, long-term tracking of individuals and high-profile, punitive enforcement intended to manage and criminalize communities of people based on the priorities of the moment.
It seems rather that the state’s long game has been to establish a well-oiled “interoperable” machinery of databases that ensure that no matter who is in charge formally, a separate system — governed by targeting decisions, algorithms, and operating procedures — is able to expand and toggle between hidden, real-time, long-term tracking of individuals and high-profile, punitive enforcement intended to manage and criminalize communities of people based on the priorities of the moment.
Undermining sanctuary
There are numerous ways that criminalizing data is passed between local and federal law enforcement agencies. Many of these automated processes negate and circumvent hard-won “sanctuary” policies. These processes fly under the radar, taking the form of short-lived pilot programs and informal agreements that can turn into unnamed and normalized long-term practices that are embedded in technology and may even contradict formal policies.
New York is one case study in confusion. Most people, including some politicians in the state, think that local sanctuary laws prevent police collaboration with immigration enforcement. But since database sharing is automated across all 50 states, there is no true way to opt out of “collaboration.”
As the news site Documented reported, “New York state has a relatively robust sanctuary framework: only a single sheriff participates in the controversial 287(g) federal program, which deputizes local law enforcement officers — typically corrections personnel — to detain immigrants for questioning and arrests.Note en bas de page 42 A New York appellate court ruled that local law enforcement cannot honor ICE detainer requests to hold immigrants in custody for longer than their normal release times.Note en bas de page 43 Former state Governor Andrew Cuomo issued an executive order and amendment restricting state agencies’ cooperation with ICE.Note en bas de page 44
Yet, like every other US state, New York law enforcement officers and agencies use Nlets and NCIC, which pass on information (biographic or biometric) from everyone arrested for automated DHS database screening.
Separately, New York’s Division of Criminal Justice Services (part of the State Identification Bureau) also receives booking fingerprints, and they send them to ICE as well. Since 2005, DCJS has specifically notified ICE every time it receives fingerprints of a person who has previously been deported. In fact, according to the state agency’s 2009 annual report, DCJS would forward an electronic notice to LESC and a real-time Blackberry notification to ICE’s New York City fugitive apprehension unit.Note en bas de page 45 While the report and some of the technology described is old, the fundamental data-sharing structure is still in place. It remains DCJS policy to automatically forward a notification to ICE when a fingerprint taken by state authorities brings up a record that includes notice of a previous deportation.Note en bas de page 46
Similarly, since 2016 DHS’ Law Enforcement Notification System (LENS) program has allowed local law enforcement (including campus safety officers) at agencies nationwide (not just in New York) to subscribe to email alerts that flag when a migrant leaving ICE custody is released in or intends to settle within that law enforcement agency’s jurisdiction.Note en bas de page 47 That is on top of ICE sharing that information directly with State Identification bureaus and fusion centers, who in turn can notify local law enforcement agencies.
How automated criminalization works:
Street-level harassment and arrest by police is disproportionately focused on working-class Black and Latinx people, and therefore tends to screen out non- or less-criminalized populations from immigration records searches, which are initiated after arrest when a person’s fingerprints are booked. Once a person has their fingerprints booked, it is the discovery of any record that indicates foreign birth that triggers the IAQ and IAR process, which directs the weight of DHS inquiry and investigation onto that individual.Note en bas de page 48 By structuring its computer systems in this way, non-immigration law enforcement and DHS have succeeded in procedurally and extra-legally implicating birth abroad, and even international travel, as criminalizing.
Arrest and booking
Two main, known procedural pathways for automated migrant criminalization are dubbed in the parlance of law enforcement’s networked computer system the “Immigrant Alien Query” (IAQ) and “Immigrant Alien Response” (IAR). These are the computerized processes that automatically compare fingerprints collected by non-immigration police against DHS holdings in order to trawl an arrested person’s records for evidence of foreign birth, travel visa applications, historical border-crossings and previous encounters with immigration enforcement. These records, if dredged up, subject an arrested person to new or reinvigorated scrutiny, surveillance, harassment and potential arrest by ICE.
As mentioned above, database cross-checking with some DHS records became standard procedure in daily policing during the era of S-Comm implementation and has grown to encompass many more datasets since. Here, we detail a shortened version of this process, step-by-step. In the appendices, we provide a much longer detailed description of each step of this process and the databases involved.
- You get stopped by a cop. Maybe it is the result of a Stop-and-Frisk-type stop, or perhaps you were pulled over while driving a car with a broken taillight.
- The cop who stopped you demands your ID. In some states, refusing to give your name to a law enforcement officer, or not carrying government-issued identification, can itself lead to arrest.Note en bas de page 49
If you are carrying and hand over a US-issued ID or driver’s license, the cop is likely able, using the information on the ID, to access almost immediately your DMV records that provide biographical details, information about whether your license is valid or suspended, vehicle registration, car insurance information, and home address.
They, or a dispatcher, will also conduct a quick search for any open warrants that would show up in local, municipal and state databases.
- The cop may also decide to search your criminal history in additional federal databases. They may be able to conduct this search from their car or via mobile device, or ask a dispatcher to do it for them.
The databases they likely consult include: National Crime Information Center (NCIC) and Nlets
-
You are arrested and taken to jail for booking. Your fingerprints are automatically checked against state-level and FBI files. When your information and biometrics are loaded into the computer system, an automatic process is triggered. Your prints, photo, and biographical information are automatically forwarded to the State Identification Bureau (which are like FBIs at the state level that archive fingerprints and criminal history). Your biometrics are checked against FBI holdings, as well as the FBI’s NCIC and Next Generation Identification (NGI) biometric databases.Note en bas de page 50
Databases implicated: NGI and NCIC
ICE nerve centers: Law Enforcement Support Center and Pacific Enforcement Response Center
The Law Enforcement Support Center (LESC) and Pacific Enforcement Response Center (PERC) are two of a handful of ICE data centers that run 24/7 to follow as many leads as possible generated by the automated data criminalization process following a law enforcement encounter and database match. ICE claims that LESC workers process approximately 1.5 million biometric and biographic (IAQ) queries annually. Following a series of automated searches of at least sixteen visa, citizenship and criminal legal databases, the LESC analyst will recommend to an ICE deportation officer whether or not the person being searched may be removable, and whether a detainer, or immigration hold, could be issued.Note en bas de page 51 LESC works closely with law enforcement and local Field Offices to provide information about people who are held in custody and whom ICE may be able to target.
- Nlets checks your biometrics against DHS’ IDENT/ HART biometric database. If anything indicates that you might be foreign-born, your profile is forwarded on to ICE analysts via a biometric or biographic “Immigrant Alien Query,” or IAQ.
If DHS has any biometric record of you in its massive database — which may have come from applications for an immigration “benefit” like a travel visa, naturalization or asylumNote en bas de page 52 — then Nlets automatically creates a biometric “Immigrant Alien Query,” or IAQ, which notifies ICE and law enforcement of the “match.” Alternatively, a biographic IAQ is created if your biometric information cannot be matched to DHS’ holdings, but if you were born outside of the US (or if DHS’ records don’t show where you were born).
Both kinds of IAQ trigger a rapid and multi-step process created by ICE to automate the creation of detainers — a notice to law enforcement that ICE is supposedly investigating a person in law enforcement custody for violating immigration laws, and a request to notify ICE if that person is going to be released.
Databases used: IDENT/ HART
- ICE analysts at the Law Enforcement Support Center in Williston, Vermont receive the IAQ from Nlets.Note en bas de page 53 IAQs are placed in a queue. Once an IAQ rises to the top of the queue, a contract analyst for ICE picks it off of the line, conducts cursory initial database queries, and begins working on an Immigrant Alien Response (IAR). The contract analyst uses a computer system, ACRIMe, and oversees the process of checking you against numerous government and private datasets.Note en bas de page 54
- ACRIMe automatically searches for name and date of birth matches in various criminal, customs, and immigration databases.Note en bas de page 55
Databases and systems used and searched can include: ACRIMe, Nlets, CIS (Central Index System)Note en bas de page 56 , CLAIMS 3 and 4, EID (Enforcement Integrated Database), EAGLE (EID Arrest Graphical User Interface for Law Enforcement) , ENFORCE, ENFORCE Alien Removal Module (EARM), Prosecutions Module (PM), OM², Law Enforcement Notification System (LENS), EDDIE, IDENT/ HART, ADIS (Arrival and Departure System), SEVIS (Student and Exchange Visitor Information System), and EOIR (Executive Office for Immigration Review)
Court documents from 2017 indicated that ICE relies on sixteen databases.Note en bas de page 57 (This statement might downplay the fact that because many databases link to others, making contact with a system like EID may actually provide datasets from a dozen or more discrete databases.) - Based on the above searches, ICE’s data analyst at LESC decides whether ICE has the basis to issue a detainer or arrest you. The ACRIMe user finalizes the Immigration Alien Response (IAR) that recommends to an ICE deportation officer whether you might be removable.Note en bas de page 58 The IAR includes a person’s last known immigration or citizenship status, basic biographical information and criminal history. ACRIMe then electronically returns the IAR to both the requesting agency and the ICE ERO Field Office that is in the region of the requestor. If the analyst decides that a person might be deportable, then an ICE agent or officer can lodge a detainer via the ACRIMe system, and the IAR is routed to the local ICE field office which has jurisdiction.Note en bas de page 59 Whatever the decision, an ICE field office can still carry out its own search, and has unchecked power to decide when the “evidence” it has is enough to justify a detainer or arrest.Note en bas de page 60
- The IAR is sent from LESC to an ICE field office, and/or PERC. ACRIMe allows contract analysts at PERC to search multiple criminal legal, DHS and commercial databases to cross-check for any possibility of deportability. ICE field officers can access the analyst’s research via ACRIMe as well, and can also conduct their own research and investigation.
PERC is a newer center, established in January 2015.Note en bas de page 61 ICE contract analysts at PERC attempt to identify, locate, and build a case against people whom it suspects are deportable. This includes people who have been previously ensnared by the automated data criminalization system, but were released before ICE picked them up. PERC creates detainers all day and night, scraping datasets that collect everything from social media posts to family members’ naturalization records to try to justify “probable cause” for a detainer.
An ongoing lawsuit, Gonzalez v. ICE, called into question whether issuing detainers based on incomplete and inaccurate databases violates the constitution, and enjoined several states, temporarily preventing them from honoring PERC detainers. A Ninth Circuit ruling in September 2020 overturned the prior injunction, but as of February 2022, ICE agreed to honor the injunction voluntarily for a 6-month period (through August 2022) during settlement negotiations.Note en bas de page 62
Additional databases consulted by PERC analysts may include: Commercial databases CLEAR and/or LexisNexis - ICE uses ACRIMe to issue a detainer to the jail where you are held. Your fate is in the hands of your jailers.
Best case scenario: Even if the cops do not honor ICE’s detainer, and you are released, your “permanent record” is now beefed up and freshly linked to criminalizing data. If you encounter law enforcement or immigration officials in the future, it will only take a quick database check for them to decide that you’re worth detaining and investigating further. Also, ICE could decide at any time to prioritize coming for you. They have very updated information about where to find you.
Worst case scenario: If the jail decides to hold you or notify ICE about the details of your release, ICE could send over an agent to arrest you.
Anyone can be in a gang database
Allegations of gang membership — which may look like having your name show up in any of the various gang databases across the country — sweep more than a million people nationally into a feedback loop of data criminalization.
Different agencies define “gang” differently. NCIC defines a "gang" broadly: as “a group of three or more persons with a common interest, bond, or activity characterized by criminal or delinquent conduct.”Note en bas de page 63
Gang databases typify some of data criminalization’s most egregious characteristics. It is possible to be in a gang database and not know about it. Maintained in secret, with entries often based entirely on the subjectivity of a law enforcement officer, these databases track and share extra-legal and unproven information about alleged gang membership, listing the names of individuals convicted of “gang-related” crimes, as well as people who have not been convicted of anything but are alleged to be “associates.” If you are close to people who are alleged to be gang members, or if you simply exist in community with people profiled as gang members, your clothing choices or “frequenting gang areas” (even if these include your own home) are likely to land you in a gang database.Note en bas de page 64 Inclusion in a gang database makes you extra visible to police for harassment — and all police encounters can easily lead to arrest, further criminalization, and possibly deportation. Lack of transparency and procedures to challenge database entries makes it all but impossible to challenge your inclusion, and data sharing across agencies makes eradicating the taint of one-time inclusion nearly impossible.
The modern chapter of using alleged gang affiliation to enhance or multiply punishment dates back to at least the 1980s, when California began establishing gang injunctions — probation-like civil orders that target certain neighborhoods. If you’re hanging out or live in a targeted neighborhood, a gang injunction allows law enforcement to arrest you for standing on the corner with a member of your family or a friend.Note en bas de page 65 Once listed as a “gang member,” you may receive longer sentences if you do get convicted of anything.Note en bas de page 66 Accusations of gang affiliation can determine where you are incarcerated, and heighten your risk of violence in jail or prison, as well as in your country of origin if you are deported.Note en bas de page 67
Being criminalized as a gang member doesn’t end after your enhanced sentence. In states like California, a person who is convicted with a gang enhancement must register as a gang member for at least five years post-incarceration.Note en bas de page 68 If you are a noncitizen, gang affiliation can make you a DHS priority and ineligible for a green card, DACA, or other benefits, and potentially lead to your deportation. Indeed, it is not uncommon for ICE to continue pursuing someone indefinitely, even after they win their immigration case, based on asserted gang affiliation.Note en bas de page 69
The mid aughts saw the major expansion of gang database creation and sharing across federal agencies. In 2005, Congress established the National Gangs Intelligence Center (NGIC), an interagency network with representatives from the FBI, ICE, and CBP, among others.
Image Source Note en bas de page 70
Soon after the creation of NGIC, in 2007 Congress authorized the Gang Abatement and Prevention Act.Note en bas de page 71 The national database established pursuant to the 2007 bill became what is now GangNet — database software owned by a federal contractor, General Dynamics, which powers databases that contain personal information about “suspected gang members, including gang allegiance, street address, physical description, identifying marks, tattoos, photographs, and nationality.”Note en bas de page 72 Although GangNet itself has been superseded in importance by a more distributed and decentralized network of local, state, and regional gang information sharing initiatives, this section focuses on GangNet as the turning point in which data criminalization related to gang allegations shifted into a new phase, and in some ways it is emblematic of developments that have followed.
GangNet offers data analysis, facial recognition software, mapping, a field interview form, and a watch list. Using a single command, agencies can simultaneously search their own GangNet system and a network of GangNet systems in other states and federal agencies. ICE and the FBI, among other law enforcement agencies, use GangNet to track and share information across agencies.
For a short time during the Obama administration, ICE had its own ICEGangs database, based on the GangNet software. Its use was discontinued, and many ICE databases since include fields to input gang information, including EID and Palantir’s ICM. ICE agents can also access the FBI's National Crime Information Center (NCIC) — which has its own gang file connected to NGIC — in several different ways.Note en bas de page 73
Additionally, ICE’s Homeland Security Investigations (HSI) stores gang investigation information in Palantir’s ICM, which is an upgraded version of CBP’s border entry-exit log database, TECS. The agency uses another Palantir product, FALCON, which accesses, duplicates, and reiterates alleged gang information from other key criminalization databases such as EID.Note en bas de page 74
At the local and state levels there are countless gang databases used and shared, from “in-house” county police departments to statewide databases like CalGang in California, which listed 80,000 people as gang members. A 2015 audit found that law enforcement “could not substantiate “a significant proportion of people in the database,” including dozens of infants tagged with “self-admission of gang membership.”Note en bas de page 68 In 2020, the state Attorney General revoked LAPD’s access to the state gang database due to CalGang’s egregious errors, and facing allegations of racial profiling.Note en bas de page 75 But LAPD continues to operate and update its own citywide gang database.Note en bas de page 76 And the Palantir products listed above allow cops to note and track “gang members” and perform searches — which cross-check local school district records and license plate location history — by entering in an alleged member’s name.Note en bas de page 77
Despite ongoing organizing against them, gang databases continue to be used by both police and ICE as methods and justification for targeting the people profiled in them. Because of database sharing and carve-outs in most legislation, local or state sanctuary laws don’t even attempt to protect people who are alleged to be gang members.
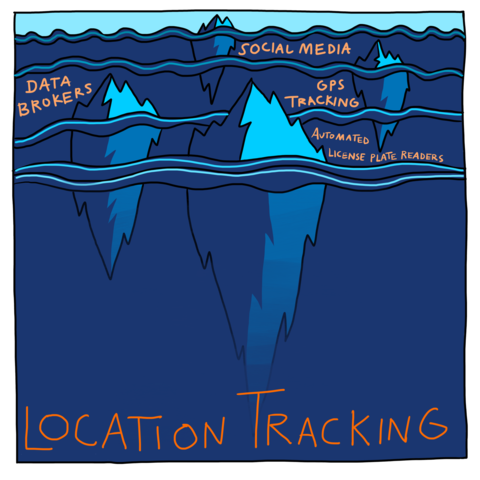
Stalking you now: Data brokers, cell phone apps, social media and GPS tracking
Location Tracking: Data brokers, automated license plate readers, social media and GPS tracking
As long as surveillance capitalists and others are permitted to steal and sell our real-time and historical location data, this information will be available to anyone who can buy it — including DHS and other government agencies.
As long as surveillance capitalists and others are permitted to steal and sell our real-time and historical location data, this information will be available to anyone who can buy it — including DHS and other government agencies.Note en bas de page 79
If you have a cell phone, you are being stalked and your personal data sold by multiple companies whose names you’ve likely never heard.Note en bas de page 80 So-called “third-party vendors” or data brokers like Venntel, Babel Street, Cuebiq, and LocationSmart collect real-time location data via GPS.Note en bas de page 81 They monitor your activities and movements through your phone via benign-seeming apps that use software development kits, or SDKs.Note en bas de page 82 Apps that use SDKs include weather apps, exercise monitoring apps, and video games.Note en bas de page 83 Third-party vendors provide SDKs to app developers for free in exchange for the information they can collect from them, or a cut of the ads they can sell through them. The aggregate information that apps collect can be extremely revealing.
There are endless examples of app data being used far outside of anyone’s initial understanding. For example, one third-party vendor, Mobilewalla, claimed to be able to track cellphones of protesters, and said it could identify protesters’ age, gender, and race via their cell phone use.Note en bas de page 84 In another case, historical location extracted by a data vendor from the gay hookup app, Grindr, was used by two reporters to “out” a top Catholic Church official.Note en bas de page 85
Law enforcement agencies regularly purchase criminal history reports, financial data from credit bureaus, and other personal data to profile people.Note en bas de page 86 For example, CBP purchases access to the Venntel global mobile location database via a portal, so that CBP officers can search a Venntel database to look for addresses or cell phones.Note en bas de page 87 DHS can also access cell phone location history from private databases that sell subscriptions or search platforms, such as LexisNexis and TransUnion.Note en bas de page 88
Some experts have noted that “anonymized” GPS location data is notoriously easy to cross-reference.Note en bas de page 89 A New York Times op-ed posed the question: “Consider your daily commute: Would any other smartphone travel directly between your house and your office every day?” The authors concluded: “In most cases, ascertaining a home location and an office location was enough to identify a person.”Note en bas de page 90 Indeed, cell phone location “pings,” collected by apps and stored under profiles tied to mobile ad IDs that are assigned to smartphones, were sufficient to identify individuals who ransacked the Capitol building in Washington, D.C., on January 6, 2020.Note en bas de page 91 And the prosecutorial use of “geo-fencing,” i.e. obtaining information from private companies about all persons in an area at a given time, has become exponentially more common in recent years.Note en bas de page 92
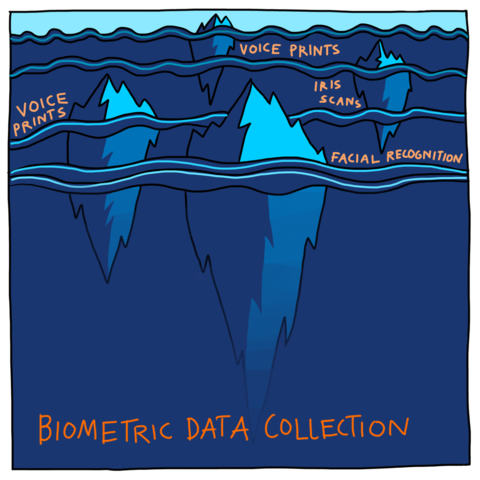
Biometrics: Cataloguing as control
Biometric Data Collection: "Facial recognition," "Voice prints," "Iris scans," "Fingerprints"
Data criminalization tracks and categorizes you relentlessly — but for that to be meaningful, you must be identifiable.
The origins of using biometric data to criminalize can be traced back to two key Victorian-era sociological practices: anthropometry, the cataloguing of national, metropolitan and colonial subjects based on physical measurements recorded by authorities and used to identify individuals; and eugenic ideas that physical attributes could prove racial inferiority as well as criminality (“mental degeneracy”) — which was thought to be a hereditary trait.Note en bas de page 93 Prisons, asylums, and forced sterilization were institutional responses to these 19th and early 20th century criminological concepts, and are the precursors to many of today’s carceral, “treatment”- and “reform”-based approaches to “criminal justice.”
Image Source Note en bas de page 94
During the last two decades since 9/11, biometric identification practices have become routine.
Our fingerprints, palmprints, faces, irises, voices, and gait are increasingly (and often secretly) recorded and used by commercial and government agencies, devices like our iPhones, and are purported to be incontrovertible, objective methods to prove our identities. Biometric identification methods are often trained on biased datasets.Note en bas de page 95 Algorithms can fail to account for changes in bodily appearance, dis/ability and gender, but as the nexus of biometric datasets expands and is able to cross-reference other tracking data, technologies such as facial recognition allow anyone who can access surveillance camera footage the ability to identify and track our movements in the world in real time.Note en bas de page 96
IDENT: DHS’ biometric data vacuum
DHS and CBP have heavily invested in biometric data theft and stalking as a primary method to surveil and criminalize all foreign-born people who enter into the US. Since the 1990s, the government has systematically collected and stored biometrics from immigrants.Note en bas de page 97 In 1994, DHS’ precursor established IDENT, or the Automated Biometric Identity System, to collect biometric data (at the time, fingerprints) from people accused of trying to enter the US without authorization.
IDENT became the central DHS-wide system for the storage and processing of biometric data, and after 9/11 it began including biometric records from people who have had any contact with DHS, including visa applicants at US embassies and consulates, noncitizens traveling to and from the United States, noncitizens applying for immigration “benefits” including asylum, migrants apprehended by CBP at the border or at sea, suspected immigration law violators encountered or arrested within the US, US citizens approved to participate in DHS's “trusted traveler” programs like Global Entry or TSA PreCheck, and people who have adopted children from abroad. IDENT also grandfathered into its database the fingerprint records for many naturalized US citizens who were fingerprinted before naturalizing, and noncitizens with current visas.
The future of IDENT = HART
HART is a present-day iteration of the anthropometric project which began with mugshots taken and catalogued in 1888.
HART is a present-day iteration of the anthropometric project which began with mugshots taken and catalogued in 1888.Note en bas de page 98
IDENT is expected to be replaced by the Homeland Advanced Recognition Technology (HART) system, a multi-billion dollar upgrade that would exponentially expand the agency’s capacity to collect, share and analyze a scaled-up and expanded range of biometric data, to be stored on Amazon Web Services’ GovCloud.Note en bas de page 99 (In this report, in order to make clear the evolution of this biometric system and reduce the number of acronyms, we refer to “IDENT/HART” when describing planned functionalities for the data system, and “IDENT” for current and previous versions of this data system.)
HART will dramatically expand DHS’ capacity to archive biometric data and search multiple modes simultaneously (face recognition and fingerprints at the same time, for instance). According to comments submitted to DHS’ Privacy Office by the Electronic Freedom Frontier, “DHS also plans to vastly expand the types of records it collects and stores to include at least seven different biometric identifiers, such as face and voice data, DNA, and a blanket category for ‘other modalities.’”Note en bas de page 100 HART allows its users to “ascertain the identity (1) of multiple people; (2) at a distance; (3) in public space; (4) absent notice and consent; and (5) in a continuous and on-going manner.Note en bas de page 101
HART will allow “latent fingerprints” (taken from surfaces, not just during booking) to be uploaded from non-immigration criminal punishment agencies. Latent prints can be archived for future searches.Note en bas de page 102 Like many DHS databases, it allows a user to subscribe to notifications if someone’s profile in HART logs a new “encounter” with DHS, or if other information in their record changes.
HART will draw directly from records created from travelers to and from the US, employment documents, and applications for other immigration “benefit” applications, as well as the FBI NGI system, which stores biometrics, including photographs, taken from state Department of Motor Vehicles.Note en bas de page 103 Similar to other DHS systems, HART will be used with other databases by DHS to collect and store “records related to the analysis of relationship patterns among individuals,” including “non-obvious relationships.” The data in the system will include records on US citizens and permanent residents as well as other non-citizens.Note en bas de page 104
Additionally, DHS spent hundreds of millions of dollars setting up state and local surveillance systems, including cameras in public places that record the daily routines and travel of millions of people.Note en bas de page 105 There are more than 30 million such surveillance cameras in the US; they are operated by both public agencies and private entities, and integrated with databases including the FBI’s main biometric repository, Next Generation Identification (NGI, formerly IAFIS) — which also feeds into various DHS databases.Note en bas de page 106
DHS under the Biden administration withdrew a Trump-era proposal that would have required more applicants (including children) for immigrant “benefits” such as asylum and student visas to submit an expanded range of biometric information including eye scans, voiceprints, DNA, and photographs for facial recognition.Note en bas de page 107 However, CBP and ICE continue to collect DNA from persons who are detained, using Buccal Collection Kits provided by the FBI Laboratory. CBP and ICE send the collected DNA samples to the FBI, which in turn process them and store the resulting DNA profile.”Note en bas de page 108
HART may become the largest biometric database in the US and the second largest in the world, and is eventually expected to store, potentially match and share DNA information.Note en bas de page 109 As a Just Futures Law report on HART notes, the database would “create a massive invasive catalog of the diverse physical characteristics of millions of US residents and people outside the United States.”Note en bas de page 110
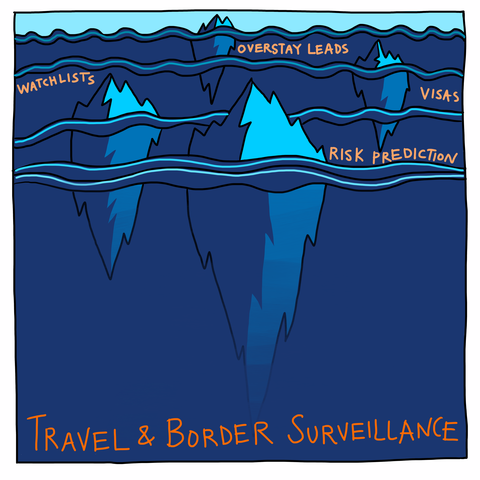
Traveler and border surveillance
"Travel and Border Surveillance": Watchlists, Risk Prediction, Visas, "Overstay Leads"
The evolution of traveler surveillance by the US government is a cautionary tale showing how obsessive focus on “identification” technologies and automated “risk” prediction can normalize biometric data theft and the presumption of criminality until it is taken for granted and universally applied.
The evolution of traveler surveillance by the US government is a cautionary tale showing how obsessive focus on “identification” technologies and automated “risk” prediction can normalize biometric data theft and the presumption of criminality until it is taken for granted and universally applied.
There is no law or regulation that requires anyone to show any ID in order to fly domestically in the US.Note en bas de page 111 Yet, for most people, refusing to do so is a sure way to miss a flight, and can lead to arrest after the TSA calls the cops.
A good two decades before ICE figured out that it could circumvent search warrants by simply buying location and personal data from commercial third-party vendors, DHS’ precursor, the Immigration and Naturalization Service (INS), was by 1998 already digitally stalking airline travelers using records created by online airplane ticket purchases, and profiling them based on their ticket-purchasing habits.Note en bas de page 112 By September 11, 2001, the government was already keeping files in a database that archived not only where you flew and when, but also the special meals you may have requested, the contact numbers you provided, and the itinerary of your journeys that did not involve air travel, such as bus and train rides.Note en bas de page 113
Before automated profiling became the norm in the criminal legal system to determine the “risk” level of people detained pretrial, and well before “constant vetting” algorithmic tools were used to predict which foreign exchange students may overstay their visas, CBP pioneered threat modeling software at US borders, rating the risk level of trade goods and people entering the country.
Traveler surveillance and border securitization, especially after 9/11, created a template for automated data criminalization practices that are widespread in criminal punishment and immigrant tracking systems today.
Early DHS digital stalking
Airline reservations have been computerized since the 1980s. As access to the Internet became a reality for more people during the 1990s, online flight reservations and other travel bookings created digital pathways for the federal government to track the movements of both citizens and non-citizens.
Over the decades, DHS sub-agencies and their predecessors accessed computerized reservation records from which they extracted Advance Passenger Information (API) and later, copies of complete Passenger Name Records (PNR) from airlines or third-party computerized reservations reservation systems.
Advance Passenger Information (API) includes information linked to the machine readable zone of passports and other travel documents, such as full name, date or birth, gender, passport number, country of citizenship, and country of passport issuance. Passenger Name Records (PNR) include the information that API records contain, and may also include a traveler’s home address, travel itineraries, credit card numbers, email addresses, IP addresses and timestamp, telephone numbers, emergency contact information, seat assignment, and other travel details. US Customs Service, a legacy organization of Customs and Border Patrol, began receiving API data voluntarily from air carriers in 1997, and after 9/11 demanded PNR data. This effectively gave DHS complete, aggregated mirror copies of the customer relationship management and transaction databases of the entire airline industry.
DHS also discovered that it could also acquire PNR data from third-party vendors to whom airlines outsourced booking; that arrangement foreshadows today’s warrant-free data-trawling via commercial data brokers.
By the late 1990s, the US Customs Service was using “computerized tools” to predict whether cargo entering, exiting, and transiting the US might violate US laws.Note en bas de page 114 Initially, risk-prediction tools were only used to screen conveyances and the people whose jobs it was to deliver trade goods. By 1999, all international travelers entering the US were evaluated like objects and profiled for “risk” by the agency’s black box analysis system. PNR data — that hodgepodge commercial airline archive of meal requests, bus trip itineraries, landline contact numbers, and credit card transactions — combined with records of border crossings, interactions with customs officers, and criminal legal data, were used as variables to screen for threats and fodder to train the algorithms. This was a key conceptual and legal shift.
Cashing in on “risk” after 9/11
“For terrorists, travel documents are as important as weapons.” — 9/11 Commission Report
The kind and amount of information collected from airline passengers who take flights within, to and from the US internationally — as well as even just over the US — changed dramatically after 9/11. While travel by non-US citizens had long been treated as inherently suspicious, prior to 9/11, most US citizens were used to traveling without being treated like a potential terrorist. Overnight, that changed. The presumption that a traveler had a legal claim to privacy and free movement, unimpeded by invasive bodily searches and x-ray scans, was replaced by the now-normal protocols that we all routinely endure in order to board a flight. While long lines, pat-downs and shoe removals are annoying for everyone, few of us have realized the ways that we’re surveilled before and after we leave the airport, and how the extent to which we’re constantly evaluated as security threats (in real time, by multiple, interlocking systems) legitimates the ever-expanding surveillance apparatuses of state and social control.
After 9/11, the federal government ramped up its data-collecting, database-sharing, automated predictive threat modeling and terrorist risk profiling. It beefed up its biometric identification technologies and partnerships with commercial entities that secretly collect, retain and sell consumer data for profit. It was a perfect storm: the World Trade Center attacks allowed the government to exceptionalize sites of travel (especially international flights) as deserving of extreme surveillance; meanwhile, big data collection and analysis industries, facilitated by growing Internet and cell phone use, were handed billions of dollars in research and development funds, and enjoyed little to no oversight as they churned out new data-collecting and prediction technologies. The US government spent at least $2.8 trillion on counterterrorism related efforts between 2002 and 2017, granting contracts to old time war profiteers like Boeing, Lockheed Martin, and Northrop Grumman — but also to tech and Silicon Valley giants such as Amazon, Google, and Palantir Technologies.Note en bas de page 115
Meanwhile, agencies that administratively managed visas for temporary stays, citizenship and naturalization were reorganized into a more bellicose Department of Homeland Security. DHS bulked up its biometric database, IDENT (now in process of upgrading to HART), by requiring biometric data collection at every point along the border and ports of entry—and extending well outwards from the national border line — from all people entering or exiting the country, non-citizens and citizens alike.
Between 2001 and 2014, IDENT added new categories of people to a list of “national security interest:” people who had any contact with DHS, related agencies, and other governments; visa applicants at US embassies and consulates; noncitizens traveling to and from the United States; noncitizens applying for immigration “benefits” (including asylum and short-term visas); unauthorized migrants apprehended at the border or at sea; suspected immigration law violators encountered or arrested within the US; and even US citizens approved to participate in DHS's “trusted traveler” programs or who adopted children from abroad.
Between 2001 and 2014, IDENT added new categories of people to a list of “national security interest:” people who had any contact with DHS, related agencies, and other governments; visa applicants at US embassies and consulates; noncitizens traveling to and from the United States; noncitizens applying for immigration “benefits” (including asylum and short-term visas); unauthorized migrants apprehended at the border or at sea; suspected immigration law violators encountered or arrested within the US; and even US citizens approved to participate in DHS's “trusted traveler” programs or who adopted children from abroad. IDENT now trolls all migrants who come to the US.
Each time that an individual’s biometric identifier is uploaded to the IDENT database by an agent for ICE, CBP, Citizenship and Immigration Services (CIS), or the Department of State, IDENT would log the data transfer as an “encounter.”Note en bas de page 116 In the circular loop of data criminalization, each of these “encounters” (which really just indicate that a person may be a non-US citizen traveler or migrant) comes up as criminalizing material when in future searches by law enforcement that data automatically flags a person for ICE agents and LESC analysts who are searching for deportability. In this way, “encounters” that fail to prove administrative law-breaking nonetheless confer suspicion on a person, marking them and even their contacts for ongoing surveillance and repeated harassment.
In this way, “encounters” that fail to prove administrative law-breaking nonetheless confer suspicion on a person, marking them and even their contacts for ongoing surveillance and repeated harassment.
CBP’s current surveillance system relies on compelled and often covert biometric identification and constant vetting against criminalizing databases during travel — using “a traveler’s face as the primary way of identifying the traveler to facilitate entry and exit from the United States” via CBP apps, kiosks for “trusted traveler” programs and security camera live feeds.Note en bas de page 117 The goal, then-CBP Commissioner Kevin McAleenan declared in 2018, is to “confirm the identity of travelers at any point in their travel,” not just at entry to or exit from the United States.Note en bas de page 118
Soon, if not already, DHS and other law enforcement agencies will be able to access more experimental modes of biometric via cloud-based IDENT/HART, to link fingerprints, palm prints, iris scans, and photographs with biographic information to construct detailed and holistic portraits. This trove of biometric data, in turn, will likely be fodder to develop and train newer technologies as they emerge.
How automated traveler surveillance works
"Risk-o-meter"
Today, all passengers are pre-screened before even stepping into an airport. You are designated “low risk” only if you have already submitted to and passed a “trusted traveler” clearance program. You might be profiled as an “unknown risk” if you did not qualify for “trusted traveler” status, or you might be deemed “high risk” based on the secret and fluctuating rules created by DHS programs like “Silent Partner” and “Quiet Skies.” These programs are mutant descendants from the War on Terror: TSA does not claim that the people who are flagged by the programs are known or suspected terrorists, and claims that being assessed as a risk does not leave a derogatory mark on a person’s record; nonetheless, being flagged by a TSA rule opens up a person’s profile for close scrutiny as the entirety of their digital histories are cross-referenced with criminalizing records — and the designation, whether or not temporary, will be noted for the future.
Anyone who is crossing a US border or traveling internationally by air, either to, from, within, or over the US is subjected to travel surveillance via:
- database-matching to watchlists and “derogatory information” stored in criminalizing government databases, updated multiple times from the time of booking until travel ends
- Internet stalking by commercial ticketing and reservation systems and airlines — all of which share information with DHS
- Real-time biometric identification and location-tracking during travel by cameras operated or accessed by airlines and CBP
- In-person interrogations and searches during travel and at border crossings
CBP uses travel industry IT and communications vendors databases and systems to siphon information as well as to control the movements of travelers in real time by denying entry or requiring in-person screening.Note en bas de page 119
“Life cycle” of international travel surveillance
As mentioned above, the process of screening all people who travel to, from, within, or even over the US begins well before anyone steps into an airport. Surveillance, identification, cross-checking and prediction processes may begin with the click of a mouse on someone’s home computer in a country far away. Here, we detail a shortened version of this process, step-by-step. We also have a longer version of this process written-up in more detail as an appendix.
- If you are a non-citizen, before you can legally enter the US you must apply for a visa and/or have your passport checked. If you were born in one of the 38 countries that qualify for the US’ visa waiver program, you don’t need a visa for some short-term visits.
If you were born in a country that is not eligible for visa waivers, you must obtain authorization, in the form of a non-immigrant or immigrant visa, from the US Department of State (DOS), issued at an US Embassy or Consulate. Visa applications automatically generate multiple biographic and biometric checks against multiple criminalizing and suspected terrorist databases that seek to verify an applicant’s identity and match them to derogatory information.Note en bas de page 120
Databases used to approve or “vet” visas: Electronic System for Travel Authorization (ESTA) and Consular Consolidated Database (CCD).
Additionally, CBP’s National Targeting Center (NTC) “continuously vets” all holders of immigrant and non-immigrant visas of travelers before they board US-bound flights. - As soon as you purchase your airline ticket, your reservation information and itinerary become available to DHS.
This information is stored and retrievable as the following data: Passenger Name Record (PNR) - Your personal profile and information — your name, ethnicity, national origin, travel itinerary, occupation, personal, political, religious and professional contacts and associations — can be screened by DHS using black-box, rules-based algorithmic predictions as well as matched against various secret watchlists. These secret and changing rules determine whether and how you may be targeted for harassment and arrest once you do show up at the airport.
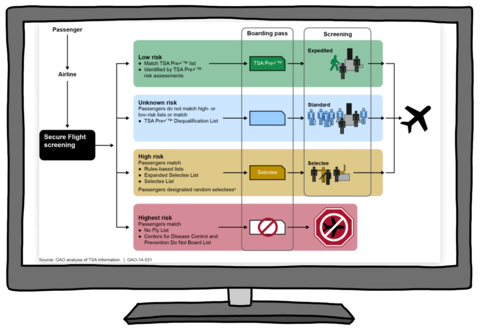
In November 2001, then-President Bush signed the Aviation and Transportation Security Act into law, creating the Transportation Security Administration (TSA) — a division of DHS that operates a travel-permission system for domestic US flights called “Secure Flight.”
“Secure Flight” began as a program where aircraft operators screened names from passenger reservations to see if they matched or closely resembled any included on a “No Fly List”Note en bas de page 121 and other federal watchlists of “known or suspected terrorists” created by the FBI. If the aircraft operator suspected a watchlist match, the operators were supposed to notify TSA and send the targeted passenger for enhanced in-person screening.
Today, “Secure Flight” allows TSA to access CBP’s surveillance dragnet and prediction tool — Automated Targeting System, or ATS, (more on this below) and write rules for the algorithm used by the ATS system to decide who qualifies as a “risk” and will be added to a category of people who will be subject to increased security checks. Targeting rules, and therefore the people targeted, can change day to day.Note en bas de page 122
According to a 2019 PIA on ATS: “These rules are based on risk factors presented by a given flight and passenger, the level of screening for a passenger that may change from flight to flight. Travelers may match a TSA or CBP-created rule based upon travel patterns matching intelligence regarding terrorist travel; upon submitting passenger information matching the information used by a partially-identified terrorist; or upon submitting passenger information matching the information used by a Known or Suspected Terrorist.”Note en bas de page 123
Data systems you are screened against and processed by may include:
- Secure Flight
- Various FBI “no fly lists,” including “known or suspected terrorists”
- Automated Targeting System (ATS): more below
- ICM/ TECS
Image Source Note en bas de page 124
Passenger, Airline, Secure Flight Screening; Low risk: Match TSA Precheck list, Identified by TSA precheck final assessments; Unknown risk: Passengers do not match high- or low- risk lists or match TSA Precheck Disqualification List, High Risk: Passengers Match, Rules-based lists, Expanded Selectee List, Selectee List, Passengers designated random selectees, Highest Risk: Passengers match, No Fly List, Centers for Disease Control and Prevention Do Not Board List
- Once you are inside the airport, your face is overtly and covertly captured for facial recognition and real-time tracking.
CBP uses its own in-house facial recognition matching technology, the Traveler Verification Service (TVS), for identity verification and biometric entry and exit “vetting checks.”Note en bas de page 125
When the traveler enters or exits an airport, border crossing, or seaport, they will pass a camera connected to CBP’s cloud-based TVS facial matching service. The camera may be owned by CBP, the air or vessel carrier, another government agency (like TSA), or an international partner.Note en bas de page 124 If the camera is CBP-owned and operated, a CBP officer will be present.
However, if the camera is airline-operated, it may not necessarily be visible. It may be located on a jetway after a passenger scans their boarding pass, and the passenger might not even know an image of their face is being captured. TVS matches the live image of the traveler on the jetway with existing photos in a “gallery” (maintained in IDENT) that archives photographs from CBP’s ATS-UPAX database that might be from previous exits and entries, US passports and visas, from DHS apprehensions, enforcement actions, or other immigration-related records.
If your face does not match existing DHS records, you are flagged for scrutiny as well. A CBP website provides the following example:
“The biometric system alerted the officers because when preflight information was gathered on the woman, no historical photos to match against her could be found.
A CBP officer took the woman aside and looked at her passport. No visa was attached and the woman didn’t have a green card to prove she was a lawful permanent resident. Upon further questioning, the woman admitted that four years ago, she had come into the country illegally.
Using a specially designed, CBP biometric mobile device, the officer took fingerprints of the woman’s two index fingers. ‘This was the first time that we had captured this individual’s biometrics, her unique physical traits,’ said Bianca Frazier, a CBP enforcement officer at the Atlanta Airport. ‘We didn’t have her biometrics because we had never encountered her before.’”Note en bas de page 126 - CBP must approve every single passenger before an international flight departs, arrives in, or overflies the US. When you check in for an international flight to, from, or that overflies the US, the Advance Passenger Information System (APIS) transmits your PNR data and itinerary (including flight status updates) to CBP. Before you are permitted to board the plane, your passport or ID is scanned by a CBP officer or TSA agent. The machine readable zone of your document pulls up your full name, date of birth, and citizenship, which can be used to retrieve information about your scheduled flight. This data is sent to CBP via APIS in the form of “passenger manifests” — commercial airline records that are transferred to CBP for vetting in real-time, or 30 minutes prior to boarding.Note en bas de page 127 APIS generates a “Overstay Lead” list that is shared with CBP’s main computer system that assesses “risk,” ATS (more on this below).Note en bas de page 128
Inside DHS’ future-prediction arsenal
Technologies are always upgrading. Here, we examine more closely two data systems that incorporate multiple future-facing elements, including geospatial and relationship-mapping visualizations and “trend detection” in addition to “risk” prediction.
Automated Targeting System (ATS)
As mentioned earlier, Automated Targeting System (ATS) is one of the most important connective databases for current migrant data criminalization processes. CBP uses ATS to assess “risk” and track travelers and import trade goods.Note en bas de page 130 CBP’s National Targeting Center uses ATS to conduct “continuous vetting” of valid US immigrant and nonimmigrant visas, and uses data from immigration, law enforcement, commercial, and open-source databases to predict “risk.”Note en bas de page 131 Continuous vetting occurs in real-time and describes the process by which ATS alerts CBP, for instance, if a traveler’s ID check at a foreign airport brings up biographical or biometric matches to any records in criminalizing databases — including those that track immigration violations, the FBI’s Terrorist Screening Database (TSDB) and outstanding wants and warrants.Note en bas de page 132 All the people who categorically fit CBP’s targeting rules are flagged by ATS, and these individuals are then reviewed by CBP officers. CBP can then issue a “no board” recommendation to prevent someone’s travel to the US, or recommend the State Department revoke a visa.
ATS’ black-box algorithms are based on criteria and rules developed by CBP, to match people and trade goods against “lookouts” and data-scrape personal information from various linked databases to identify “patterns of suspicious activity” and predict potential terrorists, transnational criminals, people who may be inadmissible to the US under US immigration law, and “persons who pose a higher risk of violating US law.”Note en bas de page 132 ATS has built its dataset over decades, well before 9/11. ATS-Passenger (ATS-P), a legacy subsystem of ATS, has been used to screen international passengers on planes, trains and ships since the 1990s — although data collection for ATS overall was expanded and automated since 2002.Note en bas de page 133 ATS-P is now being upgraded to UPAX, which more seamlessly integrates databases by showing records from multiple systems and incorporating information from third-party databases and the Internet.Note en bas de page 132
In order to train its risk assessment, ATS uses data including: bills, entries, and entry summaries for cargo imports; shippers’ export declarations and transportation bookings and bills for cargo exports; manifests for arriving and departing passengers and crew; airline reservation data; nonimmigrant entry records; and records from “secondary referrals,” CBP incident logs, suspect and violator indices, state Department of Motor Vehicle Records, and seizure records.
Every person who leaves or enters through a US border is subject to ATS’ risk assessment, and while different linked databases claim to delete data at different times, much ATS data is kept for decades, whether in ATS’s databases or mirrors and backups in other DHS systems.
Like other data criminalization tools, ATS draws heavily from NCIC data — but it also surveils people who have never had an encounter with police.Note en bas de page 134 A speaker at a 2004 Customs Budget Authorizations hearingNote en bas de page 135 testified that ATS data scrapes airline passenger information to look for “anomalies and red flags.” Since “red flags” are determined based on rules for ATS that are created by CBP, these rules allow CBP to expand the list of what is considered suspicious activity to encompass any number of legal behaviors.Note en bas de page 136 People who are deemed “high risk” by ATS are flagged for further scrutiny and sent to secondary screening at US border and airport checkpoints. Those encounters lead to the generation of yet more data criminalization records, in the form of risk assessments retained by ATS, which are fed into the targeting algorithm that could alert a TSA or CBP agent the next time the person’s passport is scanned.
Since “red flags” are determined based on rules for ATS that are created by CBP, these rules allow CBP to expand the list of what is considered suspicious activity to encompass any number of legal behaviors.
The evolution of ATS’ targeting rules reveals the trajectory of terrorism and surveillance rhetoric. Mass surveillance that began as exceptional (the post-9/11 period) and provisional (pilot programs at 15 airports) is now routine — and probable cause for law enforcement intervention (which can end in arrest and deportation) includes not only subjective suspicion but fully abstracted prediction mathematics. Today, ATS is utilized by CBP to predict who might violate US immigration (not just anti-terrorism) laws: ATS data is used to generate an “Overstay Hotlist,” which is a list of “overstay leads” derived from information obtained through travel records.Note en bas de page 137 (More on this below.)
Mass surveillance practices in travel have normalized data criminalization entirely, effectively making de facto criminalization the norm, rather than an exception. A 2020 DHS report on data mining explained: “When evaluating risk, ATS is designed to apply the same methodology to all individuals to preclude any possibility of disparate treatment of individuals or groups.”Note en bas de page 138 Literally, what that means is that everyone begins their journey evaluated as a suspect.
Literally, what that means is that everyone begins their journey evaluated as a suspect.
Feeding the beast: Electronic devices searches and ATS
Warrantless searches of electronic devices, such as cell phones and laptops, are currently permitted at US borders and part of the process that accumulates material and trains algorithms for data criminalization.Note en bas de page 141
An ATS Privacy Impact Assessment from May 2020 explains: “Searches can be vital to risk assessments that otherwise may be predicated on limited or no advance information about a given traveler or item, and they can enhance critical information sharing with, and feedback from, elements of the Federal Government responsible for analyzing terrorist threat information. Digital information extracted from electronic devices and saved in ATS may relate both to the owner of the device, as well as his or her contacts.”Note en bas de page 132
DHS can make use of extracted or copied digital data from electronic devices in multiple ways. The ATS-TF (Targeting Framework) module allows users to perform research and analysis by integrating data from multiple sources, including from electronic devices, and to show possible relationships between entities and data elements. CBP can also pass on the information to AFI, a continuous vetting system, designed by Palantir, “to develop leads.” (More on this below.)
LeadTrac, SEVIS, ADIS and ATS
LeadTrac is a HSI database that vets and manages “leads” of people in the US whom a DHS algorithm flagged as being likely to overstay or violate their visas.Note en bas de page 143
A person who has overstayed their visa is first tracked through CBP’s Arrival and Departure Information System (ADIS), which is used at entry and exit points, and includes photos, biographical and visa information, including the end date for an authorized stay. For people such as students on indefinite visas, ADIS data is supplemented with other systems that perform ongoing tracking such as ICE’s Student and Exchange Visitor Information System (SEVIS). ADIS combines data from multiple sources and sends “leads” to ATS. CBP agents, ICE agents and other law enforcement can also add people directly into the ATS system.Note en bas de page 144 DHS manually processes information from ADIS to trawl for overstays, but ATS conducts its own (black box) algorithmic risk-assessment to generate a list of prioritized targets for LeadTrac.
AFI: CBP’s Extreme Vetting data-mapping system
Analytical Framework for Intelligence (AFI) is another Palantir tool, described as a web-based information technology system. It uses profiling algorithms created for former President Trump’s “Extreme Vetting” initiativeNote en bas de page 145 to “detect trends, patterns, and emerging threats, and identify non-obvious relationships between persons, events, and cargo.”Note en bas de page 146 According to a 2012 PIA on AFI, “data is indexed so that the system may retrieve it by any identifier maintained in the record. As information is retrieved from multiple sources it may be joined to create a more complete representation of an event or concept. For example, a complex event such as a seizure that is represented by multiple records may be composed into a single object, for display, representing that event.”Note en bas de page 147 In this way, AFI offers data visualization, and creates an index.
Among other data points, AFI uses and stores public records showing who owns land near the US - Mexico border, and ingests records on “individuals not implicated in activities in violation of laws enforced or administered by CBP but with pertinent knowledge of some circumstance of a case or record subject,” as well as those not accused of breaking immigration or other laws but who might have “knowledge of narcotics trafficking or related activities.”Note en bas de page 148 In 2019, AFI made headlines when NBC reported that AFI was being used to mine US citizens’ social media posts on “caravans” and political rallies in order to train its targeting algorithm.Note en bas de page 149
AFI provides tools like geospatial, temporal and statistical analysis, and advanced search capabilities of commercial databases and Internet sources, including social media and traditional news media. Like other DHS systems, AFI automatically collects and stores criminalizing data from travel records in ATS-UPAX, ESTA, ADIS, ICM/ TECS, records from immigration arrests and deportations, and lists of foreign students. AFI also copies volumes of such government data onto its own (Palantir) servers.Note en bas de page 150 AFI uses Apache Hadoop, an open source framework that allows for faster searching across big datasets, which is hosted on the Amazon cloud. Hadoop requires continuous replication of data stored in multiple locations as well.Note en bas de page 151
Bureaucracy and exclusion: Naturalization, asylum and other USCIS “benefits”
Constant Vetting: Visa Application, Social Media Stalking, Background Checks, Relationship Mapping
As noted, simply being foreign-born, being racially and nationally profiled by law enforcement as a potentially deportable immigrant, or having records in immigration or visa files can trigger a chain of events that self-reinforce and lead from inclusion into data criminalization databases to arrest and deportation based on criminalizing data matches.
Unlike the traditional criminalization arms of DHS, USCIS’ stated purpose is to provide “benefits” — whether it’s citizenship, permanent status, temporary status, permission to apply for status, or work and travel authorization. But when USCIS receives an application for most of these benefits, it undertakes an extensive investigation of the person applying — and sometimes of others related to that person — that taps into dozens of databases across many agencies. This can lead directly to data criminalization, and USCIS readily turns information over to ICE for arrests when it sees fit.Note en bas de page 152 Further, ICE can access the systems built to give USCIS information about an applicant, such as the Person Centric Query Service (PCQS), a key CIS database that ICE uses to surveil, arrest, and deport people. Finally, USCIS undertakes its own investigations, expanding the capacity of the data criminalization apparatus within immigration agencies as a whole.Note en bas de page 153
An application-based dragnet
If you’ve submitted an application for immigration “benefits,” USCIS uses PCQS to pull information from over 20 databases — including DHS databases, other federal agency databases, and private databases — to gather information about you. Many applications to USCIS require appearing at an “application support center” so USCIS can collect biometric information including facial photographs and fingerprinting, which are used to cross-check federal databases.Note en bas de page 154 But even for applications that don’t require biometrics, USCIS cross-checks the information provided through the application forms, including identity documents.
That information can then be used to criminalize or even denaturalize you.Note en bas de page 155 USCIS devised and uses data-mining software called ATLAS (which is part of its Fraud Detection and National Security Data System, or FDNS) to automatically and sometimes continuously screen all applicants and their social networks against the FBI Terrorist Screening Database, NCIC, ATS,Note en bas de page 156 and other DHS databases.Note en bas de page 157 ATLAS searches for the potential for the government to revoke citizenship or legal status from a person by harvesting criminalizing information about them from databases and then visually displaying “linkages or relationships among individuals to assist in identifying non-obvious relationships… with a potential nexus to criminal or terrorist activities.”Note en bas de page 158
As a result, depending on the information and your circumstances, filing an application can trigger an ICE raid at your home if DHS decides they can deport you right away, or USCIS may invite you for an interview only to have ICE arrest you at their office.Note en bas de page 159 Or, if USCIS denies the application, they may refer the matter to ICE and issue a “Notice to Appear” in immigration court to start deportation proceedings.Note en bas de page 160
People who are filing family- or fear-based applications are particularly vulnerable under the 2011 “referral” guidance that remains in effect today, whereas people who were beneficiaries of employment petitions are far less likely to be referred to ICE upon denial of an application by their employer.Note en bas de page 161
Even if an application is approved, the risk of data-driven criminalization does not end: recently uncovered FOIA documents and reporting revealed that ICE has access to information about when DACAmented folks’ work authorization periods end at the field office level, which could allow individual field offices to keep tabs on someone and arrest them if their status lapses.Note en bas de page 162 This contradicts promises from the government that DACA information would not be used for enforcement, and USCIS specifically tried to hide this information from Congress.Note en bas de page 163 In some cases, such as with Special Immigrant Juvenile Status applications and some types of sponsorship of unaccompanied children, the surveillance extends beyond the immediate applicants to include others as well—in that case, every adult household member of the guardian/custodian of the applicant must be fingerprinted and subjected to background checks.
At any point, USCIS can refer a case to its own investigators in its Fraud Detection and National Security Directorate (mentioned above). FDNS has extremely broad authority to access records available to DHS from internal or external government databases, and generate its own records by interviewing people, issuing subpoenas, requesting law enforcement assistance, and making site visits or telephone calls.Note en bas de page 164 Notably, FDNS spearheaded DHS’s social media surveillance program dating back to at least 2008.Note en bas de page 165 It continues to rely on social media monitoring, including through the creation of fake accounts, to this day. Starting in 2017, the FDNS announced that it would not only use social media information for individual investigations, but also that it would start including social media information in the “A File” records system as it collected data.Note en bas de page 166 (FDNS also offers freestanding support to other law enforcement agency investigations).Note en bas de page 167
From background checks to continuous criminalization
USCIS applicants are also checked against ATS — CBP’s aggressive “risk assessment” system that claims to predict potential visa overstays and future law violators.Note en bas de page 168 USCIS will use the information provided by ATS and other CBP databases to identify individuals “who may have a connection to potential identity or benefit fraud, national security or public safety concerns, and criminal activity.” The details of their screenings are included in the database for future checks. Through “continuous vetting,” or continuous criminalization, “individuals connected to a USCIS immigration application benefit request” will be subject to security checks upon receipt by USCIS and CBP, and ATS will stop recurrent vetting only when it receives a message from USCIS based on administrative closure from an Immigration Judge’s calendar or from the Board of Immigration Appeal docket, certificate of citizenship issue, denial, failure to pay, or withdrawn adjudication activities.
In addition to form submission information, USCIS will send to CBP biographic, biometric identifiers, and encounter information from IDENT/HART. ATS is already able to retrieve these data elements through its existing IDENT/HART interface.
Continuous vetting expands the current background check processes by automating screening and vetting the information against additional CBP databases and establishing recurrent checks against these datasets.
- 1 a Office of Inspector General, U.S. Immigration and Customs Enforcement’s Criminal Alien Program Faces Challenges, February 18, 2020, https://www.oig.dhs.gov/sites/default/files/assets/2020-02/OIG-20-13-Fe….
- 2 a Office of Inspector General, U.S. Immigration and Customs Enforcement’s Criminal Alien Program Faces Challenges, February 18, 2020, https://www.oig.dhs.gov/sites/default/files/assets/2020-02/OIG-20-13-Fe….
- 3 a Joan M. Jensen, Army Surveillance in America, 1775–1980 (New Haven, CT: Yale University Press, 1991).
- 4 a Office of Inspector General, Potentially Ineligible Individuals Have Been Granted U.S. Citizenship Because of Incomplete Fingerprint Records, September 8, 2016, 4, https://www.oig.dhs.gov/assets/Mgmt/2016/OIG-16-130-Sep16.pdf
- 5 a Leisy Abrego et al., “Making Immigrants into Criminals: Legal Processes of Criminalization in the Post-IIRIRA Era,” Journal on Migration and Human Security 5, no. 3 (September 1, 2017): 694–715, https://doi.org/10.1177/233150241700500308.
- 6 a César Cuauhtémoc García Hernández, Migrating to Prison: America’s Obsession with Locking Up Immigrants (2019).
- 7 a Human Rights Watch, “US: 20 Years of Immigrant Abuses,” April 25, 2016, https://www.hrw.org/news/2016/04/25/us-20-years-immigrant-abuses.
- 8 a National Immigration Project of the National Lawyers Guild and Immigrant Justice Network, “The INA's Distorted Definition of ‘Conviction,” May 14, 2021, https://nipnlg.org/PDFs/practitioners/practice_advisories/crim/2021_14M….
- 9 a National Immigration Project of the National Lawyers Guild and Immigrant Justice Network, “Aggravated Felonies and the Harmful Exclusion of People from Immigration Relief,” April 21, 2021, https://nipnlg.org/PDFs/practitioners/practice_advisories/crim/2021_21A….
- 10 a Three main collaborative programs have been notable in normalizing data criminalization: the Criminal Alien Program (CAP), 287(g), and Secure Communities (S-Comm). We detail these below, but it is worth noting that while historically, ICE arrests and removals were sometimes recorded and attributed to a specific program like S-Comm, since 2017, ICE stopped reporting on S-Comm removals altogether. Therefore, at this point, it may not be meaningful to differentiate between S-Comm and CAP in particular. The CAP umbrella encompasses a wide range of collaborations (as described below), and at this point both CAP and S-Comm processes have been made universal in police practices.
- 11 a Office of Inspector General and U.S. Department of Homeland Security, Operations of United States Immigration and Customs Enforcement’s Secure Communities, April 2012, 3, https://www.oig.dhs.gov/assets/Mgmt/2012/OIG_12-64_Mar12.pdf.
- 12 a Muñiz, “Bordering.”
- 13 a Defendants’ Response to Plaintiffs’ Rule 56-1 Statement of Uncontroverted Facts and Conclusions of Law at 10, Gonzalez v. Immigr. & Customs Enf't, 416 F. Supp. 3d 995 (C.D. Cal. 2019) (No. 2:12-cv-09012-AB-FFM), ECF No. 287 (“IAQ’s are also automatically generated whenever a fingerprint pertaining to a person with a foreign or unknown place of birth does not match any record in DHS’s fingerprint repository.").
- 14 a Dara Lind, “Inside the Government's Most Powerful Weapon for Deporting Unauthorized Immigrants,” Vox, November 2, 2015, https://www.vox.com/2015/11/2/9657806/criminal-alien-program#:~:text=Fr….
- 15 a American Immigration Council, “The Criminal Alien Program (CAP): Immigration Enforcement in Prisons and Jails,” August 1, 2013, https://www.americanimmigrationcouncil.org/sites/default/files/research….
- 16 a Lind, “Inside the Government's Most Powerful Weapon.”
- 17 a Eisha Jain, “Jailhouse Immigration Screening,” Duke Law Journal 70, no. 8 (May 2021), https://scholarship.law.duke.edu/cgi/viewcontent.cgi?article=4075&conte….
- 18 a Guillermo Cantor, et al., Enforcement Overdrive: A Comprehensive Assessment of ICE’s Criminal Alien Program, 2015, https://www.americanimmigrationcouncil.org/sites/default/files/research….
- 19 a American Immigration Council, “The Criminal Alien Program” and Transactional Records Access Clearinghouse, “Historical Data: Immigration and Customs Enforcement Removals,” 2016, https://trac.syr.edu/phptools/immigration/removehistory/.
- 20 a “The Criminal Alien Program (CAP): Immigration Enforcement in Prisons and Jails,” August 1, 2013, https://www.americanimmigrationcouncil.org/sites/default/files/research….
- 21 a Cantor, et al., Enforcement Overdrive.
- 22 a Lind, “Inside the Government's Most Powerful Weapon for Deporting Unauthorized Immigrants.”
- 23 a Transactional Records Access Clearinghouse, “ICE Immigration Raids: A Primer,” February 13, 2017, https://trac.syr.edu/immigration/reports/459/.
- 24 a Transactional Records Access Clearinghouse, “ICE Immigration Raids: A Primer,” February 13, 2017, https://trac.syr.edu/immigration/reports/459/
- 25 a U.S. Immigration and Customs and Enforcement, “Delegation of Immigration Authority Section 287(g) Immigration and Nationality Act,” April 8, 2021, https://www.ice.gov/identify-and-arrest/287g.
- 26 a The power to enter these MOUs was granted to ICE’s predecessor agency by a 1996 amendment to the Illegal Immigration Reform and Immigrant Responsibility Act.
- 27 a ICE, “Delegation of Immigration Authority Section 287(g) Immigration and Nationality Act,” 2021, https://www.ice.gov/identify-and-arrest/287g
- 28 a Immigrant Defense Project, “Ending Police Collaboration with Mass Deportation Programs: PEP, ICE out of Rikers, and Ending S-Comm,” Immigrant Defense Project website, June 22, 2016, https://www.immigrantdefenseproject.org/campaign-to-end-secure-communit….
- 29 a Transactional Records Access Clearinghouse, https://trac.syr.edu/phptools/immigration/detainhistory/
- 30 a Transactional Records Access Clearinghouse, “Latest ICE Data on Detainer Usage Updated Through April 2018,” 2018, https://trac.syr.edu/immigration/reports/522/.
- 31 a U.S. Immigration and Customs Enforcement, “ICE Detainers: Frequently Asked Questions,” accessed April 26, 2021, https://www.ice.gov/identify-and-arrest/detainers/ice-detainers-frequen….
- 32 a U.S. Immigration and Customs Enforcement, “DHS Form I-247: Immigration Detainer,” December 2012, accessed April 26, 2021, https://www.ice.gov/doclib/secure-communities/pdf/immigration-detainer-….
- 33 a Kate M. Manuel, Immigration Detainers: Legal Issues, Congressional Research Service, May 7, 2015, https://www.everycrsreport.com/reports/R42690.html.
- 34 a Gonzalez v. U.S. Immigr. & Customs Enf't, 975 F.3d 788, 799 (9th Cir. 2020).
- 35 a ICE’s version of “probable cause” is extremely broad and easy to meet, because it requires only “reason to believe, based on the circumstances, that the alien has violated federal immigration laws.” Hillel R. Smith, Immigration Arrests in the Interior of the United States: A Primer, Congressional Research Service, June 3, 2021, https://crsreports.congress.gov/product/pdf/LSB/LSB10362.
- 36 a Hillel R. Smith, Immigration Detainers: Background and Recent Legal Developments, Congressional Research Service, October 9, 2020.
- 37 a National Immigration Forum, “The Legal Questions Around Immigration Detainers,” February 27, 2019, https://immigrationforum.org/article/legal-questions-around-immigration….
- 38 a TRAC noted in 2017 that ICE claims not to track whether it picked up a person from custody following a detainer, and contends that it only knows when a detainer is prepared and does not track whether it was actually issued. Likewise, ICE says that its data systems do not allow it to track whether the detainer actually led to the removal, or whether the removal was the result of other unconnected enforcement efforts.
- 39 a Transactional Records Access Clearinghouse, “The Role of ICE Detainers Under Bush and Obama,” February 1, 2016, https://trac.syr.edu/immigration/reports/458/.
- 40 a TRAC, “Secure Communities.”
- 41 a Transactional Records Access Clearinghouse, “The Role of ICE Detainers Under Bush and Obama,” February 1, 2016, https://trac.syr.edu/immigration/reports/458/
- 42 a Liz Robbins, “A Lone New York Sheriff Signs Up to Aid Immigration Crackdown,” New York Times, March 20, 2018, https://www.nytimes.com/2018/03/20/nyregion/new-york-rensselaer-county-….
- 43 a Yancey Roy, “Court: Suffolk sheriff illegally detained inmate for ICE,” Newsday, November 14, 2018, https://www.newsday.com/news/region-state/vincent-demarco-susai-francis….
- 44 a Felipe De La Hoz, “New York, a Sanctuary State, Provides Criminal Justice Data to ICE,” Documented, May 8, 2019, https://documentedny.com/2019/05/08/new-york-a-sanctuary-state-provides….
- 45 a Sean M. Byrne, New York State Division of Criminal Justice Services 2009 Annual Performance Report, 2010, https://www.criminaljustice.ny.gov/pio/annualreport/2009-annual-dcjs-pe….
- 46 a Immigrant Defense Project and New York Civil Liberties Union, “New York Practice Advisory: When Does Fingerprinting Put Your Client at Risk with ICE?,” Immigrant Defense Project, July 27, 2017, https://www.immigrantdefenseproject.org/wp-content/uploads/DCJS-advisor….
- 47 a U.S. Department of Homeland Security, “Privacy Impact Assessment Update for the Enforcement Integrated Database (EID) Law Enforcement Notification System (LENS) DHS/ICE/PIA-015(g),” September 22, 2015, https://www.dhs.gov/sites/default/files/publications/PIA%2C%20ICE-EID%2….
- 48 a Even if no record is discovered at all—called a “no-match”—it is still possible to initiate a search, but it is less automatic and universal. ICE, “Secure Communities: Standard Operating Procedure,” undated, https://www.ice.gov/doclib/foia/secure_communities/securecommunitiesops….
- 49 a Immigrant Legal Resource Center, “Stop and Identify Statues in the United States,” February 1, 2018, https://www.ilrc.org/sites/default/files/resources/stop_identify_statut….
- 50 a “Section 15: Criminal History Record Information Transactions (CHRI),” Nlets Wiki.
- 51 a The databases, identified in May 2019 court testimony in the Gonzalez v. ICE trial, include: IDENT, CIS, CLAIMS 3 and CLAIMS 4, ADIS, SEVIS, TECS, EOIR, EID, ENFORCE/EARM, SQ11, SQ94, ELIS 1 & 2, the California Birth Index, CCD, RAPS, and the NCIC and NLETS databases.
- 52 a Department of Homeland Security, “Privacy Impact Assessment for the Homeland Advanced Recognition Technology System (HART) Increment 1 PIA,” February 24, 2020, https://www.dhs.gov/sites/default/files/publications/privacy-pia-obim00….
- 53 a Agencies submit IAQs to inquire about an individual’s citizenship and/or immigration status.
- 54 a U.S. Immigration and Customs Enforcement, “Enforcement and Removal Operations: LESC, PERC, and NCATC Fact Sheet,” May 11, 2020, https://www.ice.gov/doclib/about/offices/ero/pdf/todCenterOverviews.pdf.
- 55 a U.S. Department of Homeland Security, “Alien Criminal Response Information Management System (ACRIMe),” April 22, 2010, 4, https://www.dhs.gov/sites/default/files/publications/privacy-pia-ice-02….
- 56 a U.S. Department of Homeland Security, “DHS/USCIS/PIA-009 Central Index System,” https://www.dhs.gov/publication/dhsuscispia-009-central-index-system.
- 57 a Gonzalez v. U.S. Immigr. & Customs Enf't, 975 F.3d 788, 821 (9th Cir. 2020).
- 58 a According to the ACRIMe PIA from September 2018, “ICE has expanded the users of ACRIMe beyond the LESC to include ERO officers located at the Pacific Enforcement Response Center (PERC) as well as in ERO field offices and command centers across the country.” DHS, “PIA for ACRIMe,” September 28, 2018.
- 59 a DHS, “PIA for ACRIMe,” September 28, 2018, 2.
- 60 a By law, ICE must have a “reason to believe” someone is in violation of immigration law, 8 U.S.C. § 1357, and courts uniformly conclude that “reason to believe” is the same as “probable cause” for arrest. But there is no external check on ICE’s decision to arrest or issue a detainer, and there is no real consequence when ICE fails to follow this standard, so in practice, ICE can arrest people when it deems fit, on any basis it deems fit, as seen with the targeted arrests of anti-deportation activists in recent years.
- 61 a “Pacific Enforcement Response Center (PERC),” ICE website, accessed April 26, 2021, https://www.ice.gov/video/pacific-enforcement-response-center-perc.
- 62 a Gonzalez, 975 F.3d at 826. Under the agreement, ICE says that, for cases identified through PERC, it will not issue database-only detainers, i.e. request that a jail or prison extend someone’s incarceration time to allow ICE to arrest them before release based only on information in (a) database(s). However, ICE reserved the right to use database-only results as the basis to: (1) use a different form of detainer to request notice from the jail of someone’s release, (2) do additional investigation (such as interviewing someone in the jail) to find an “independent” basis for a detainer, or (3) issue database-only detainers from local offices, if the case was never routed or flagged through PERC.
- 63 a “National Crime Information Center (NCIC) - FBI Information Systems,” June 2, 2008, https://fas.org/irp/agency/doj/fbi/is/ncic.htm.
- 64 a Immigrant Legal Resource Center ,“Understanding Allegations of Gang Membership/Affiliation in Immigration Cases,” April 2017, 4, 6, https://www.ilrc.org/sites/default/files/resources/ilrc_gang_advisory-2….
- 65 a Ryan Devereux, “Marked Man: An ICE Informant, MS-13, and the Long Campaign to Deport Walter Cruz-Zavala,” The Intercept, May 1, 2021, https://theintercept.com/2021/05/01/ice-detainee-deportation-walter-cru….
- 66 a Maritza Perez, “Mistaken Identity,” Center for American Progress (blog), September 13, 2018, https://www.americanprogress.org/issues/criminal-justice/reports/2018/0….
- 67 a Janaé Bonsu and Andy Clarno, Tracked and Targeted: Early Findings on Chicago’s Gang Database, Policing in Chicago Research Group, February 2018, 9, http://erasethedatabase.com/wp-content/uploads/2018/02/Tracked-Targeted….
- 68 a b Perez, “Mistaken Identity.”
- 69 a Devereux, “Marked Man.”
- 70 a Ali Winston, “Marked for Life: U.S. Government Using Gang Databases to Deport Undocumented Immigrants,” The Intercept, August 11, 2016, https://theintercept.imgix.net/wp-uploads/sites/1/2016/07/SRA-internati….
- 71 a “Press Release: Senate Unanimously Approves Feinstein-Hatch Comprehensive Gang Legislation,” United States Senator for California, Dianne Feinstein, September 21, 2007, https://www.feinstein.senate.gov/public/index.cfm/2007/9/2984b4b3-01dd-….
- 72 a Immigrant Legal Resource Center, “Understanding Allegations of Gang Membership/Affiliation in Immigration Cases,” 4.
- 73 a National Immigration Project, Immigrant Defense Project, and Mijente, “Who’s Behind ICE? The Tech and Data Companies Fueling Deportations,” October 23, 2018, 12, https://www.nationalimmigrationproject.org/PDFs/community/2018_23Oct_wh….
- 74 a U.S. Department of Homeland Security, “Operation Raging Bull Field Guidance,” 2017, https://mijente.net/wp-content/uploads/2019/07/HSI-Operation-Raging-Bul….
- 75 a Anita Chabria and Kevin Rector, “California AG Revokes Police Access to LAPD CalGang Data,” GovTech c/o Los Angeles Times, July 15, 2020, § Justice and Public Safety, https://www.govtech.com/public-safety/California-AG-Revokes-Police-Acce….
- 76 a “GSS Overview & Mission,” Official Site of the Los Angeles Police Department (LAPD), undated, https://lapdonline.org/special_operations_support_division/content_basi….
- 77 a Caroline Haskins, “Scars, Tattoos, And License Plates: This Is What Palantir And The LAPD Know About You,” BuzzFeed News, September 29, 2020, https://www.buzzfeednews.com/article/carolinehaskins1/training-document….
- 79 a “Buy SDK Location Data,” Datarade, undated, https://datarade.ai/data-categories/sdk-location-data.
- 80 a Alex Pasternack and Steven Melendez, “Here Are the Data Brokers Quietly Buying and Selling Your Personal Information,” Fast Company, March 2, 2019, https://www.fastcompany.com/90310803/here-are-the-data-brokers-quietly-….
- 81 a Charles Levinson, “Through Apps, Not Warrants, 'Locate X' Allows Federal Law Enforcement to Track Phones,” Protocol, March 5, 2020, https://www.protocol.com/government-buying-location-data.
- 82 a Sara Morrison, “The Hidden Trackers in Your Phone, Explained,” Vox, July 8, 2020, https://www.vox.com/recode/2020/7/8/21311533/sdks-tracking-data-location.
- 83 a Josh Hafner, “While You Track Pokémon, Pokémon Go Tracks You,” USA Today, July 13, 2016, https://www.usatoday.com/story/tech/nation-now/2016/07/11/while-you-tra….
- 84 a Caroline Haskins, “Almost 17,000 Protesters Had No Idea A Tech Company Was Tracing Their Location,” BuzzFeed News, June 25, 2020, https://www.buzzfeednews.com/article/carolinehaskins1/protests-tech-com….
- 85 a Shoshana Wodinsky, “A Priest Was Outed by His Phone's Location Data. Anyone Could Be Next.,” Gizmodo, July 21, 2021, https://gizmodo.com/a-priest-was-outed-by-his-phones-location-data-anyo….
- 86 a Aaron Rieke et al., Data Brokers in an Open Society, November 2016, https://www.opensocietyfoundations.org/uploads/42d529c7-a351-412e-a065-….
- 87 a Joseph Cox, “CBP Bought ‘Global’ Location Data from Weather and Game Apps,” VICE, October 6, 2020, https://www.vice.com/en/article/n7wakg/cbp-dhs-location-data-venntel-ap….
- 88 a Biddle, “LexisNexis to Provide Giant Database of Personal Information to ICE”; Rieke et al. Data Brokers.
- 89 a Shoshana Wodinsky, “'Anonymized' Data Is Meaningless Bullshit,” Gizmodo, February 3, 2020, https://gizmodo.com/anonymized-data-is-meaningless-bullshit-1841429952.
- 90 a Thompson and Warzel, “One Nation, Tracked,” New York Times, 2019.
- 91 a Charlie Warzel and Stuart A. Thompson, “They Stormed the Capitol. Their Apps Tracked Them,” The New York Times, February 5, 2021, https://www.nytimes.com/2021/02/05/opinion/capitol-attack-cellphone-dat….
- 92 a Zack Whittaker, “Google Says Geo-Fence Warrants Make Up One-Quarter of All U.S. Demands,” TechCrunch, August 18, 2021, https://techcrunch.com/2021/08/19/google-geofence-warrants/.
- 93 a Pierre Piazza, “Alphonse Bertillon and the Identification of Persons (1880-1914),” Criminocorpus, August 26, 2016, https://criminocorpus.org/en/exhibitions/suspects-defendants-guilty/alp….
- 94 a Allison Meier, “The Mug Shot's Origins in Debunked 19th-Century Science,” Hyperallergic, April 7, 2016, https://hyperallergic.com/284250/the-mug-shots-origins-in-debunked-19th…. Bertillon, Alphonse. 1893. Identification anthropométrique: instructions signalétiques.
- 95 a “Coded Bias - How Did AI Become Racist?” DW.com, March 26, 2021, https://www.dw.com/en/coded-bias-how-did-ai-become-racist/av-57014307.
- 96 a Rosa Wevers, “Unmasking Biometrics’ Biases: Facing Gender, Race, Class and Ability in Biometric Data Collection,” TMG Journal for Media History 21, no. 2, November 1, 2018: 89–105, https://doi.org/10.18146/2213-7653.2018.368.
- 97 a Even before then, biometrics were collected on an ad hoc basis as part of enforcement actions against individuals. See generally Rachel E. Rosenbloom, Policing Sex, Policing Immigrants: What Crimmigration's Past Can Tell Us About Its Present and Its Future, 104 Cal. L. Rev. 149 (2016).
- 98 a Jeannene M. Przyblyski, “Revolution at a Standstill: Photography and the Paris Commune of 1871,” Yale French Studies, no. 101, 2001: 54–78, https://doi.org/10.2307/3090606.
- 99 a DHS initially planned to replace IDENT with HART in 2018 — but a US Government Accountability Office (GAO) report from June 2021 indicated that DHS postponed deployment of the first phase of HART for December 2021, due to mismanagement by HART’s main contractor, Northrop Grumman. United States Government Accountability Office, “Report to Congressional Requesters: DHS Needs to Fully Implement Key Practices in Acquiring Biometric Identity Management System,” June 2021, https://www.gao.gov/assets/gao-21-386.pdf.
- 100 a Electronic Frontier Foundation, “Comments of the Electronic Frontier Foundation Regarding Department of Homeland Security,” May 24, 2018, 4, https://www.eff.org/files/2018/06/14/eff_comment_dhs_external_biometric….
- 101 a Brandon Thompson, “Homeland Advanced Recognition Technology (HART) Data Collection: Fourth Amendment Considerations & Suggested Statutory Alternatives,” Southern California Interdisicplinary Law Journal 29, no. 155 (April 10, 2020): 3, https://gould.usc.edu/why/students/orgs/ilj/assets/docs/29-1-Thompson.p….
- 102 a U.S. Department of Homeland Security, “Privacy Impact Assessment for the Homeland Advanced Recognition Technology System (HART) Increment 1 PIA,” 12, https://www.dhs.gov/sites/default/files/publications/privacy-pia-obim00….
- 103 a Electronic Privacy Information Center, “EPIC Letter to FBI Oversight Senate Committee,” May 1, 2017, https://epic.org/testimony/congress/EPIC-SJC-FBIOversight-May2017.pdf.
- 104 a Electronic Frontier Foundation, “Comments.”
- 105 a Electronic Privacy Information Center, “EPIC v. FBI - Next Generation Identification,” 2019, https://epic.org/foia/fbi/ngi/.
- 106 a “IAFIS/NGI Biometric Interoperability,” FBI - Services - Information Management, June 10, 2016, https://www.fbi.gov/services/information-management/foipa/privacy-impac….
- 107 a Hamed Aleaziz, “Biden Is Going To Scrap A Trump-Era Plan To Force Immigrants To Submit Eye Scans, Voice Prints, And DNA,” BuzzFeed News, May 7, 2021, https://www.buzzfeednews.com/article/hamedaleaziz/biden-scrapping-trump….
- 108 a U.S. Department of Homeland Security, “DHS/ALL/PIA-080 CBP and ICE DNA Collection,” 2020, https://www.dhs.gov/publication/dhsallpia-080-cbp-and-ice-dna-collection.
- 109 a Jack Corrigan, “Legacy Systems Held DHS’ Biometrics Programs Back. Not Anymore.,” Nextgov, October 3, 2019, https://www.nextgov.com/it-modernization/2019/10/legacy-systems-held-dh….
- 110 a Immigrant Defense Project, Just Futures Law, and Mijente, “Freeze Expansion of the HART Database,” April 2021, https://justfutureslaw.org/wp-content/uploads/2021/04/HART-Appropriatio….
- 111 a Edward Hasbrouck, “You don’t have to show any ID to fly,” The Identity Project, December 28, 2015, https://papersplease.org/wp/2015/12/28/you-dont-have-to-show-any-id-to-….
- 112 a House of Representatives Hearing, Improving the Pre-screening of Aviation Passengers Against Terrorism and Other Watch Lists: Hearing before the Subcommittee of Economic Security, Infrastructure Protection, and Cybersecurity of the Committee on Homeland Security, 109th Cong., 1st sess., July 29, 2005, https://www.govinfo.gov/content/pkg/CHRG-109hhrg26959/html/CHRG-109hhrg….
- 113 a Edward Hasbrouck, Puck Lo Interview with Edward Hasbrouck, Phone, April 2, 2021.
- 114 a Kozanas, “DHS Privacy Office: 2019 Data Mining Report to Congress,” 19.
- 115 a Emma Knight and Alex Gekker, “Mapping Interfacial Regimes of Control: Palantir's ICM in America's Post-9/11 Security Technology Infrastructures,” Surveillance & Society, June 16, 2020, 4, https://doi.org/10.24908/ss.v18i2.13268.
- 116 a Thompson, “Homeland Advanced Recognition Technology (HART) Data Collection: Fourth Amendment Considerations & Suggested Statutory Alternatives,” 159, 161, https://gould.usc.edu/why/students/orgs/ilj/assets/docs/29-1-Thompson.p….
- 117 a U.S. Customs and Border Patrol, CBP Trade and Travel Report Fiscal Year 2020, February 2021, 8, https://www.cbp.gov/sites/default/files/assets/documents/2021-Feb/CBP-F….
- 118 a Kevin McAleenan, “Testimony of Kevin McAleenan (CBP) Before U.S. House of Representatives: ‘Border Security, Commerce and Travel: Commissioner McAleenan’s Vision for CBP’” (2018), https://docs.house.gov/meetings/HM/HM11/20180425/108207/HHRG-115-HM11-W….
- 119 a Edward Hasbrouck, “Connecting the DHS to the airline industry,” The Identity Project, April 12, 2021, https://papersplease.org/wp/2021/04/12/connecting-the-dhs-to-the-airlin….
- 120 a Testimony Before the U.S. House of Representatives Committee on Homeland Security on “Supporting a Fact-Based Approach to Preventing Terrorist Travel to the United States”, 2019, 3 (Donald Conroy, Director, National Targeting Center — Passenger Operations, U.S. Customs and Border Protection, and Monte B. Hawkins, Director, National Vetting Center, U.S. Customs and Border Protection) https://homeland.house.gov/imo/media/doc/Jt.Testimony-Conroy-Hawkins.pdf.
- 121 a U.S. Department of Homeland Security, “Privacy Impact Assessment for the Secure Flight Program,” August 9, 2007, https://www.dhs.gov/sites/default/files/publications/privacy_pia_tsa_se….
- 122 a U.S. Department of Homeland Security, “Privacy Impact Assessment for Secure Flight Silent Partner and Quiet Skies DHS/TSA/PIA-018(i),” April 19, 2019, https://www.dhs.gov/sites/default/files/publications/pia-tsa-spqs018i-a….
- 123 a “PIA for Secure Flight Silent Partner and Quiet Skies DHS/TSA/PIA-018(i).”
- 124 a b U.S. Department of Homeland Security, “Privacy Impact Assessment for the Traveler Verification Service DHS/CBP/PIA-056,” November 14, 2018, 6, https://www.dhs.gov/sites/default/files/publications/privacy-pia-cbp056….
- 125 a U.S. Department of Homeland Security, “DHS/CBP/PIA-056 Traveler Verification Service,” https://www.dhs.gov/publication/dhscbppia-056-traveler-verification-ser….
- 126 a Marcy Mason, “Biometric Breakthrough: How CBP is Meeting its Mandate and Keeping America Safe,” accessed December 15, 2021, https://www.cbp.gov/frontline/cbp-biometric-testing.
- 127 a U.S. Department of Homeland Security, “Privacy Impact Assessment for the Advance Passenger Information System (APIS): Voluntary Expansion DHS Reference No. DHS/CBP/PIA-001(i),” February 10, 2021, https://www.dhs.gov/sites/default/files/publications/privacy-pia-cbp001….
- 128 a U.S. Department of Homeland Security, “Fiscal Year 2019 Entry/Exit Overstay Report,” March 30, 2020, 9, https://www.dhs.gov/sites/default/files/publications/20_0513_fy19-entry….
- 130 a ATS began as a system to track cargo and conveyances entering the US. CBP receives electronic information on all cargo shipped to the United States 24 hours before the cargo is loaded at foreign seaports and four hours prior to arrival for air shipments. Similar data transmission requirements exist for truck and rail shipments as well. ATS processes this information, allowing the NTC to evaluate every shipment for security risks in advance. U.S. Department of Homeland Security, “Privacy Impact Assessment for the Automated Targeting System,” Kurt Stout, “National Targeting Center to Consolidate,” Colliers Government Solutions, February 11, 2014, https://www.capitolmarkets.com/agencies/dhs/national-targeting-center-c…; August 3, 2007, https://www.dhs.gov/sites/default/files/publications/privacy_pia_cbp_at…; U.S. Department of Homeland Security, “Privacy Impact Assessment Update for the Automated Targeting System DHS/CBP/PIA-006(e),” January 13, 2017, https://www.dhs.gov/sites/default/files/publications/privacy-pia-cbp006….
- 131 a Testimony on “Supporting a Fact-Based Approach to Preventing Terrorist Travel to the United States, Conroy, Director of National Targeting Center; and Hawkins, Director, National Vetting Center, 2019, 3, https://www.govinfo.gov/content/pkg/CHRG-116hhrg36398/html/CHRG-116hhrg….
- 132 a b c d “PIA Update for the ATS DHS/CBP/PIA-006(e),” January 13, 2017.
- 133 a Ellen Nakashima, “Collecting of Details on Travelers Documented,” Washington Post, September 22, 2007, https://www.washingtonpost.com/wp-dyn/content/article/2007/09/21/AR2007….
- 134 a As the PIA for ATS (January 2017) states, “ATS rules and assessment results from rules are designed to signal to CBP Officers that further inspection of a person, shipment, or conveyance may be warranted, even though an individual may not have been previously associated with a law enforcement action or otherwise be noted as a person of concern to law enforcement.”
- 135 a Hearing before the Subcommittee on Trade, 108th Congress (U.S. House of Representatives, Committee on Ways and Means), 2004 https://www.govinfo.gov/content/pkg/CHRG-108hhrg23795/html/CHRG-108hhrg….
- 136 a “PIA Update for the ATS DHS/CBP/PIA-006(e),” January 13, 2017, 112.
- 137 a Kozanas, “DHS Privacy Office: 2019 Data Mining Report to Congress,” 15.
- 138 a Kozanas, “DHS Privacy Office: 2019 Data Mining Report to Congress.”
- 141 a Adi Robertson, “Border Agents Can Search Phones Freely under New Circuit Court Ruling,” The Verge, February 10, 2021, https://www.theverge.com/2021/2/10/22276183/us-appeals-court-first-circ….
- 143 a In addition to those listed above, other database sources include NSEERS (DHS program from 2002-2011), EID, TECS, IDENT, FALCON, AFI, the Office of Biometric Identity Management’s Secondary Inspection Tool, and INTERPOL’s Criminal Data Access Management System.
- 144 a U.S. Department of Homeland Security, “Privacy Impact Assessment for LeadTrac System,” July 22, 2016, 2, https://www.dhs.gov/sites/default/files/publications/privacy-pia-ice-le….
- 145 a Knight and Gekker, “Mapping Interfacial Regimes of Control.”
- 146 a Medina and Customs, “Privacy Compliance Review of the U.S. Customs and Border Protection Analytical Framework for Intelligence (AFI) December 6, 2016,” 1.
- 147 a U.S. Department of Homeland Security, “Privacy Impact Assessment for the Analytical Framework for Intelligence (AFI),” June 1, 2012, https://www.dhs.gov/sites/default/files/publications/privacy_pia_cbp_af….
- 148 a U.S. Customs and Border Protection, U.S. Department of Homeland Security, “Notice of Modified Privacy Act System of Records: DHS/CBP-024 CBP Intelligence Records System (CIRS),” Federal Register, December 14, 2020, https://www.federalregister.gov/documents/2020/12/14/2020-27446/privacy….
- 149 a Raya Koreh, “CBP’s New Social Media Surveillance: A Threat to Free Speech and Privacy,” Brennan Center for Justice c/o Just Security, April 26, 2019, https://www.brennancenter.org/our-work/analysis-opinion/cbps-new-social….
- 150 a Woodman, “Documents Suggest Palantir Could Help Power Trump’s ‘Extreme Vetting’ of Immigrants.”
- 151 a U.S. Department of Homeland Security, “Privacy Compliance Review of the U.S. Customs and Border Protection (CBP) Analytical Framework for Intelligence (AFI),” December 19, 2014, 10, https://www.dhs.gov/sites/default/files/publications/dhs-privacy-pcr-af….
- 152 a Phyllis A. Coven, Annual Report 2021 Citizenship and Immigration Services Ombudsman, June 30, 2021, 16-17, https://www.dhs.gov/sites/default/files/publications/dhs_2021_ombudsman….
- 153 a U.S. Department of Homeland Security and U.S. Citizenship and Immigration Services, “Privacy Impact Assessment for the Enterprise Service Bus 2,” March 6, 2018, https://www.dhs.gov/sites/default/files/publications/privacy-pia-008a-U….
- 154 a U.S. Department of Homeland Security, “USCIS Electronic Immigration System (USCIS ELIS) DHS/USCIS/PIA-056(a),” December 3, 2018.
- 155 a Sam Biddle and Maryam Saleh, “Little-Known Federal Software Can Trigger Revocation Of Citizenship,” The Intercept, August 25 2021, https://theintercept.imgix.net/wp-uploads/sites/1/2021/08/FOIA-flowchar….
- 156 a U.S. Department of Homeland Security, “Privacy Impact Assessment for the ATLAS DHS Reference No. DHS/USCIS/PIA-084,” October 30, 2020, https://www.dhs.gov/sites/default/files/publications/privacy-pia-uscis0….
- 157 a Biddle and Saleh, “Little-Known Federal Software Can Trigger Revocation Of Citizenship,” The Intercept, August 25 2021, https://theintercept.com/2021/08/25/atlas-citizenship-denaturalization-….
- 158 a U.S. Department of Homeland Security, “Privacy Impact Assessment for the Fraud Detection and National Security Data System (FDNS-DS) DHS/USCIS/PIA-013(a),” May 18, 2016, https://omb.report/icr/201911-1615-011/doc/96319901.
- 159 a Regina Garcia Cano, “Federal Agents Are Using Marriage Interviews as an Immigration Trap, Lawsuit Says,” NBC News, October 8, 2019, https://www.nbcnews.com/news/latino/federal-agents-are-using-marriage-i….
- 160 a Catholic Legal Immigration Network, Inc., “USCIS Issues Revised NTA Guidance Quick Analysis,” July 9, 2018, https://cliniclegal.org/resources/uscis-issues-revised-nta-guidance-qui….
- 161 a U.S. Citizenship and Immigration Services, “Policy Memorandum: Revised Guidance for the Referral of Cases and Issuance of Notices to Appear (NTAs) in Cases Involving Inadmissible and Removable Aliens ,” November 7, 2011, https://www.uscis.gov/sites/default/files/document/memos/NTA%20PM%20(Ap…. As of this writing, enforcement priorities (which are subject to litigation and partially enjoined) may limit the number of referrals to ICE as a matter of discretion. These are subject to change at a moment’s notice.
- 162 a Dara Lind, “ICE Has Access to DACA Recipients' Personal Information Despite Promises Suggesting Otherwise, Internal Emails Show,” ProPublica, April 21, 2020, https://www.propublica.org/article/ice-has-access-to-daca-recipients-pe….
- 163 a U.S. Citizenship and Immigration Services, “Redacted Email Recommending Deletion of Statements,” September 19, 2017, https://s3.documentcloud.org/documents/6843155/9-19-2017-Redacted-Ooi-E….
- 164 a U.S. Department of Homeland Security, “Privacy Impact Assessment for the Fraud Detection and National Security Directorate DHS/USCIS/PIA-013-01,” December 16, 2014, https://www.dhs.gov/sites/default/files/publications/privacy-pia-uscis-….
- 165 a “Government Expands Social Media Monitoring of Immigration Applicants,” Deutsch, Killea and Eapen Immigration Law Firm, July 24, 2019, https://www.immigrationdc.com/blog/government-expands-sociial-media-mon….
- 166 a U.S. Department of Homeland Security, “Privacy Impact Assessment Update for the Fraud Detection and National Security Directorate DHS/USCIS/PIA-013-01(a),” July 26, 2019, https://www.dhs.gov/sites/default/files/publications/privacy-pia-uscis-….
- 167 a “Privacy Impact Assessment for the Fraud Detection and National Security Directorate DHS/USCIS/PIA-013-01,” 2014.
- Revenir au texte à partir de la note en bas de page 168U.S. Department of Homeland Security, “Privacy Impact Assessment for the Continuous Immigration Vetting,” February 14, 2019, https://www.dhs.gov/sites/default/files/publications/pia-uscis-fdnsciv-….