1. You get stopped by a cop.
Maybe it is the result of a Stop-and-Frisk-type stop, or perhaps you were pulled over while driving a car with a broken taillight.
2. The cop who stopped you demands your ID.
In some states, refusing to give your name to a law enforcement officer, or not carrying government-issued identification, can itself lead to arrest.Footnote 1
If you are carrying and hand over a US-issued ID or driver’s license, the cop is likely able, using the information on the ID, to access almost immediately your DMV records that provide biographical details, information about whether your license is valid or suspended, vehicle registration, car insurance information, and home address.
They, or a dispatcher, will also conduct a quick search for any open warrants that would show up in local, municipal and state databases.
3. The cop may also decide to search your criminal history in additional federal databases.
They may be able to conduct this search from their car or via mobile device, or ask a dispatcher to do it for them.
The databases they likely consult include: NCIC and Nlets
NCIC
This is the main criminalizing database at the federal level, owned by the FBI’s National Crime Information Center (NCIC) in Clarksburg, West Virginia. NCIC is the centralized national database for tracking “crime-related” information.
The NCIC database is accessible to law enforcement and DHS sub-agencies, directly and via a privately-owned communications system (like an advanced “Intranet”) called Nlets. In addition to listing open warrants and stolen property, NCIC has an “Immigration Violators” designation, which includes names input by ICE analysts alleged to be “deported felons” or “absconders.”
Nlets
Nlets is a communications system that shares information between 45,000 law enforcement organizations nationally and internationally, and checks the fingerprints of anyone booked by police against DHS records.Footnote 2
Like NCIC, Nlets is multiple things, and is worth examining as a target. It is private and self-funded. It is a more than fifty-year-old “partnership” of fifty states, law enforcement agencies and corporate partners.
Nlets allows police, ICE and other users of its system to query information from federal law enforcement and multiple states at once if they have a person’s name and other biographical details. Depending on varying state rules, Nlets might provide SSN and home address, parole, probation, and criminal legal history information that is additional to what can be found in NCIC and other federal and state information-sharing pipelines.
Additionally, Nlets includes and shares driver’s license photosFootnote 3 for facial recognition,Footnote 4 and motor vehicle registration information, as well as information obtained via one of ICE’s main investigative data centers, the Law Enforcement Support Center (LESC).
Nlets shares information with its partner private companies, which in turn develop surveillance technologies for law enforcement. These include an international communications network that has been operational at least since the late 1990s, and a cloud-based network that includes criminal records and personal data. It is a backbone of the data criminalization machinery.Footnote 5
ICE depends on Nlets for its automated migrant-stalking process. According to its 2020 ICE Office of Acquisition Management budget justification document, ICE stated, “Based on Market Research, no other vendor can provide the same unique services that Nlets provides to the LESC.”Footnote 6
As Just Futures Law noted in its 2020 report on Nlets, “It is important to understand that state participation in Nlets, along with many other national or regional data exchanges, is voluntary. States can choose not to share information or limit the type of information shared through Nlets. Some states have already chosen not to share certain information, such as driver’s license photos, through Nlets.”Footnote 7
4. You are arrested and taken to jail for booking.
Your fingerprints are automatically checked against state-level and FBI files.
When your information and biometrics are loaded into the computer system, an automatic process is triggered. Your prints, photo, and biographical information are automatically forwarded to the State Identification Bureau (which are like FBIs at the state level that archive fingerprints and criminal history). Your biometrics are checked against FBI holdings, as well as the FBI’s NCIC and Next Generation Identification (NGI) biometric databases.Footnote 8
Databases implicated: NGI and NCIC
NGI
The FBI’s Next Generation Identification (formerly Department of Justice Criminal Justice Information Services Division Integrated Automated Fingerprint Identification System, or IAFIS) is purportedly the largest electronic repository of biometric information in the world.Footnote 9 While historically, “biometrics” refers to fingerprints, today the category includes experimental modalities including palm prints, voice prints, irises, and facial recognition. NGI includes fingerprints that have been sent to the FBI via the criminal legal system primarily, by states, territories and federal law enforcement agencies. If you’ve ever been arrested before, you would be listed in NGI.
NCIC
Despite technically being a criminal history database, since 2001 NCIC generates a “hit” for an immigration violation if a name or other identifying information entered in an NCIC query matches records flagged by ICE.
Among those NCIC records that Nlets accesses:
- persons deported “for drug or firearms trafficking” or “serious violent crimes,”
- persons allegedly subject to a final deportation, exclusion, or removal order;
- persons who have administrative warrants for failure to comply with national security registration requirements — which may include people listed in a now-defunct “War on Terror” special registry, the National Security Entry‐Exit Registration System (NSEERS), that registered 90,000 Muslims between 2002 and 2011 and was dismantled in 2016; and
- the NCIC Gang File.Footnote 10
It is unclear exactly how detailed or accurate the NCIC information in a “hit” may be. A 2005 Migration Policy Institute report looking at police queries from 2002-2004 found that during that time the system generated erroneous immigration hits in almost 9,000 cases.Footnote 11 “The rate of false positives was 42 percent overall, and some individual law enforcement agencies had error rates as high as 90 percent,” the report stated. NCIC continues to be a main database used in automated criminalization.Footnote 12
Law Enforcement Support Center and Pacific Enforcement Response Center (sidebar)
The Law Enforcement Support Center (LESC) and Pacific Enforcement Response Center (PERC) are two of a handful of ICE data centers that run 24/7 to follow as many leads as possible generated by the automated data criminalization process following a law enforcement encounter and database match. ICE claims that LESC workers process approximately 1.5 million biometric and biographic (IAQ) queries annually. Following a series of automated searches of at least sixteen visa, citizenship and criminal legal databases, the LESC analyst will recommend to an ICE deportation officer whether or not the person being searched may be removable, and whether a detainer, or immigration hold, could be issued.Footnote 13 LESC works closely with law enforcement and local Field Offices to provide information about people who are held in custody and who ICE may be able to target.
5. Nlets checks your biometrics against DHS’ IDENT/ HART biometric database, and if anything indicates that you might be foreign-born, your profile is forwarded on to ICE analysts.
If DHS has any biometric record of you in its massive database — which may have come from applications for an immigration “benefit” like a travel visa, naturalization or asylumFootnote 14 — then Nlets automatically creates a biometric “Immigrant Alien Query,” or IAQ, which notifies ICE and law enforcement of the “match.”
Alternatively, if your biometric information cannot be matched to DHS’ holdings, but if you were born outside of the US (or if DHS’ records don’t show where you were born), a biographic IAQ is automatically created.
The IAQ triggers a rapid and multi-step process created by ICE to automate the creation of detainers — a notice to law enforcement that ICE is supposedly investigating a person in law enforcement custody for violating immigration laws, and a request to notify ICE if that person is going to be released.
Database used: IDENT/HART
IDENT/HART
ICE uses IDENT/HART to match biometric information across databases and create person-centric profiles.
Your fingerprints, and possibly your face, are checked against records kept by the Automated Biometric Identification System (IDENT) — which is being replaced by a new system, HART (Homeland Advanced Recognition Technology).Footnote 15 IDENT/ HART records biometric and biographic information of people from “encounters” with police and immigration officers.Footnote 16 It includes photographs and biographical information required from international travelers and visiting foreign nationals who applied for certificates of US citizenship and visas.
(In this report, in order to make clear the evolution of this biometric system and reduce the number of acronyms, we refer to “IDENT/HART” when describing planned functionalities for the data system, and “IDENT” for current and previous versions of this data system.)
IDENT/ HART is on pace to contain over 260 million individual’s information by 2022, and may outpace NGI to become the largest database of biometric and biographic information on citizens and foreigners in the United States. It shares information with federal agencies and state and local law enforcement agencies. HART is expected to store and process digital fingerprints, iris scans, and facial images and DNA information, and when fully implemented will link these biometrics with biographic information.Footnote 17 The main contractor developing IDENT/ HART is the war profiteer, Northrop Grumman.Footnote 18 HART would be hosted in Amazon Web Services’ GovCloud.Footnote 19
6. ICE analysts at the Law Enforcement Support Center (LESC) in Williston, Vermont receive the Immigrant Alien Query (IAQ) from Nlets.
IAQsFootnote 20 are placed in a queue. Once an IAQ rises to the top of the queue, a contract analyst for ICE picks it off of the line, conducts cursory initial database queries, and begins working on an Immigrant Alien Response (IAR). The contract analyst uses a computer system, ACRIMe, and oversees the process of checking you against numerous government and private datasets.Footnote 21
Databases used: Nlets and ACRIMe
Nlets
According to a 2020 ICE Office of Acquisition Management budget justification document,
Without access to Nlets, ICE does not have the ability to query other State and Local Law Enforcement databases for criminal records, DMV records, state court records, and numerous other state databases, and may be forced to remove over 322,000 ICE warrants from the NCIC database.Footnote 22
Furthermore, “It’s been confirmed that no other vendor is connected to Law Enforcement agencies nationwide, and can provide access to NCIC data, and allow Law Enforcement officers nationwide to submit queries, which allows the LESC to respond to the queries in a secure environment.”
ACRIMe
Once the IAQ is created, Nlets drops off.Footnote 23 A different ICE information system, ACRIMe (Alien Criminal Response Information Management System), takes over.Footnote 24 ACRIMe is a web-based, wraparound system within which ICE’s contract analysts and field officers can access some criminal legal and DHS sub-agency files, respond to immigration status queries, or tag targeted individuals in FBI and criminal law enforcement files for future “lookout.”Footnote 25
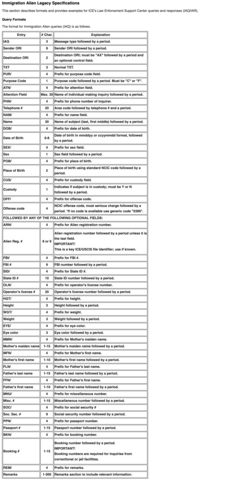
Source: Nlets Wiki
The full content of this chart can be found under the heading "Legacy (DEPRECATED: Immigration Alien Legacy Specifications" at https://wiki.nlets.org/index.php/Section_19:_Immigration_Alien_Transactions.
Source: Nlets Wiki
The full content of this chart can be found under the heading "Legacy (DEPRECATED: Immigration Alien Legacy Specifications" at https://wiki.nlets.org/index.php/Section_19:_Immigration_Alien_Transactions.
7. ACRIMe automatically searches for name and date of birth matches in various criminal, customs, and immigration databases.
Databases and systems used and searched can include:Footnote 26
-
ACRIMe allows ICE to flag individuals in the NCIC system and/ or mark their record with an outstanding criminal or administrative warrant — so that if the person is arrested in the future, the ICE note will show up.Footnote 27
- Nlets
- CIS (Central Index System)Footnote 28 - More detail below
- CLAIMS 3 and 4
- CLAIMS 3 allows an ICE officer or analyst to review a person’s applications for, among other things, lawful permanent residency, temporary protected status, and work authorization. CLAIMS 3 collects biographical information, travel and visa data, and also stores social media identifiers (also known as usernames, identifiers, or “handles”) and associated social media platforms used by an applicant during the five years prior to application.Footnote 29 Individuals familiar with CLAIMS 3 consider the database’s error rate to be close to 30 percent.Footnote 30
- CLAIMS 4 contains information from naturalization applications.Footnote 31
- EID (Enforcement Integrated Database) - more detail about the EID databases is below
- EAGLE (EID Arrest Graphical User Interface for Law Enforcement)
- ENFORCE
- ENFORCE Alien Removal Module (EARM)
- Prosecutions Module (PM)
-
OM²: Tracks location via addresses on file with utility providers and USPS
-
Law Enforcement Notification System (LENS)
-
EDDIE
- IDENT/ HART: archives biometric and biographic information (including experimental modalities such as voice and facial recognition) taken from current and past visa applications, passports, and from during individuals’ encounters with law enforcement and immigration officers.Footnote 32
- ADIS (Arrival and Departure System): ICE uses ADIS to predict, using algorithms, which non-immigrant visitors might overstay their visa, based on an individual’s entry and exit data, and their immigration status information.Footnote 33 In 2017, the DHS OIG found that ADIS incorrectly identified visa overstays more than 42 percent of the time.Footnote 34
- SEVIS (Student and Exchange Visitor Information System): ICE uses SEVIS to track noncitizens who enter the United States as students and exchange visitors, as well as their dependents.Footnote 35
- EOIR (Executive Office for Immigration Review): This DHS database provides basic information about immigration court proceedings.
The ACRIMe user at LESC can query the above databases, and also choose to manually search other government and commercial databases.Footnote 36
Court documents from 2017 indicated that ICE relies on sixteen databases.Footnote 37 (This statement might downplay the fact that because many databases link to others, making contact with a system like EID may actually provide datasets from a dozen or more discrete databases.)
More detail on some of these databases follows.
CIS (Central Index System)
This USCIS database contains biographical and status information of applicants seeking immigration and non-immigration benefits. Data in CIS is riddled with errors such as name misspellings and incorrect nationalities listed.Footnote 38 DHS acknowledged in a 2012 study that at least 12% of individuals had the wrong “admission field,” which is often caused by an officer failing to update a person’s immigration status when it changes.Footnote 39 The CIS database is the “spine” of USCIS’s functions.Footnote 39
CIS’ main purpose is to provide a searchable central index of A-Files — physical files that contain hard copy documents that detail a person’s current immigration status.Footnote 40 According to DHS, “A-Files document the life of immigrants in the United States. The average A-file includes around 200 pages; the size of A-Files is increasing and varies significantly based on the number of interactions with U.S. officials and the amount of material submitted to the government by the immigrant. While there have been some recent efforts to digitize some of the forms in A-Files, the records are largely paper-based. These records are held and processed at the National Records Center (NRC), a vast cave located in Lee’s Summit, Missouri. DHS uses a cave for NRC operations because the environment is beneficial for paper-based records, and is large enough to accommodate the amount of space needed for storage – the facility has an area of nearly six football fields. A-Files might also be located at one of hundreds of field offices around the country.” USCIS maintains millions of A-Files and has millions more in digitized format.Footnote 41
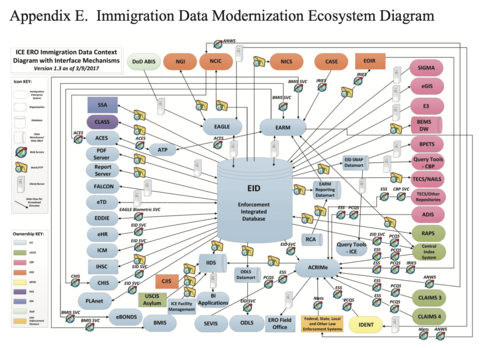
EID (Enforcement Integrated Database)
EID is a “database repository” that can only be accessed via a suite of applications, EAGLE and ENFORCE. EID is one of ICE’s most vital and generative databases for data criminalization, storing biometric and biographic information of individuals arrested and detained by ICE.
EID “talks to” and connects dozens of federal databases, creating a fractal of criminalization potential.
EID’s sources include: NCIC, suspects, victims, witnesses, and associates interviewed by DHS officers or agents; undercover operations and related surveillance technology; confidential informants; visa and immigration benefits applications, travel documents, and identification documents (i.e. visas, birth certificates); federal, state, local, tribal, international, or foreign governmental organizations; employers, schools, and universities; individuals making bond arrangements; applicants, sponsors, and those representing noncitizens during immigration benefit application processes; publicly and commercially available databases (i.e. newspapers, registries, social media); and other federal databases.Footnote 43
Source: US Immigration and Customs EnforcementFootnote 44
EAGLE (EID Arrest Graphical User Interface for Law Enforcement)
EAGLE is a booking application (a “suite”) used to access data stored in EID.Footnote 45 EAGLE allows multiple law enforcement officers and contractors in different locations (including via mobile devices) to confirm a person’s identity and access the same information simultaneously in order to research and build out a person’s biometric and biographic profile.Footnote 46 EAGLE creates records in EID.
EAGLE also submits biographic information, fingerprints, and arrest information to the FBI’s NGI biometric database (formerly IAFIS) for storage and for fingerprint-based criminal records checks. EAGLE receives the results of the fingerprint check from NGI, including any criminal history information or wants and warrants on the individual. EAGLE also submits biographic information, fingerprints, photographs, and arrest/encounter information to the DHS IDENT/ HART biometric database for enrollment and query. EAGLE will receive the results of the IDENT check, which include any matching biographic information, Fingerprint Identification Number, photographs, and previous encounter information. EAGLE receives and archives, among other things, information about foreign nationals who’ve visited the US — whose fingerprints and photographs from visa applications are stored in IDENT/ HART.Footnote 47
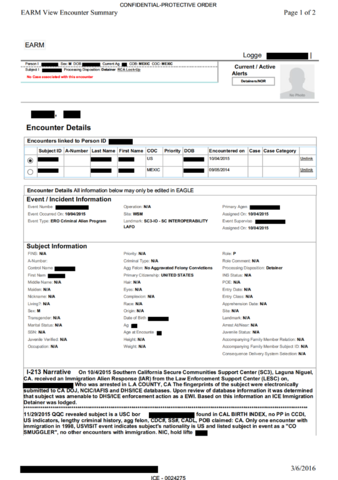
ENFORCE
ENFORCE Alien Removal Module (EARM): Records include: multiple photos to track changes in a migrant detainee’s appearance, details about phone calls made by people being detained — including information about the person who was called, the person’s relationship to the detainee, the date and length of the call, the phone number that was called, whether the call was successful, and any freeform comments made by ICE deportation officers.
EARM also records enrollment details for ICE’s ATD program, ISAP III, including the type of supervision that the individual will receive. (GPS location data collected from ISAP enrollees are stored on the contractor, B.I. Inc.’s databases.)
Prosecutions Module (PM): Tracks criminal cases by data-scraping public court records
DHS does not have one comprehensive system that tracks all criminal cases in real time and simultaneously identifies and locates individuals whose legal status make them deportable. One workaround the agency has created is the Prosecutions Module, or PM, which data scrapes information from the main US Courts online system, Public Access to Court Electronic Records (PACER).Footnote 48
PM siphons data from THE PACER system to access case and docket information online from federal district, magistrate, appellate, and bankruptcy courts.
Accessed through EARM, PM is used as part of ICE Enforcement Removal Office (ERO)’s Criminal Alien Program (CAP) “to track the status of aliens’ criminal cases as they move through the judicial system,” according to DHS’ Privacy Impact Assessment on EID in 2018. Through this method, ICE can identify when someone will have a court date and make an arrest, or wait until the final outcome of a case to determine whether the case makes someone newly vulnerable to arrest and deportation. The focus of CAP and PM is on “identification and arrest of removable aliens who are incarcerated within federal, state and local prisons and jails, as well as at-large criminal aliens that have circumvented identification.”
PM can also access real-time information from the Federal Bureau of Prisons (BOP) inmate information system (SENTRY), which shows where people serving prison sentences are held or moved.
OM²: Tracks location via addresses on file with utility providers and USPS
Operations Management Module is used by ICE ERO officers to locate and track “leads” via addresses linked to them. According to a 2019 DHS Privacy Impact Assessment, OM² performs manual and batch checks against US Postal Service commercially available data sets that update city and state information by zip code. It can cross-reference those data against commercial sources that provide open source data that includes biographical information, criminal history, criminal case history, and vehicle information (including vehicle registration information). It includes “phone numbers of targets associated with the lead.”Footnote 49
Law Enforcement Notification System (LENS): Notifies non-immigration law enforcement when people meeting certain criminalized criteria are released from ICE custody
LENS is a notification and messaging system within EARM that pulls data from EID to automatically screen people scheduled for release from ICE custody for certain “violent or serious crimes.”Footnote 50
People who meet the criteria pre-selected by ICE are targeted for informal criminalization via notifications to non-immigration law enforcement informing them of the pending release.Footnote 51
DHS acknowledged in its 2015 PIA of LENS that ICE officers rely on data from NCIC to determine “whether an alien has a qualifying conviction that triggers a LENS notification,” but alleged that “standard ICE practice” involves “validating the existence of a conviction with the primary source (e.g., the court or other appropriate source, such as a parole officer) while the alien is in ICE custody.”
According to a 2015 Privacy Impact Assessment evaluating LENS, “Book-out, criminal conviction, and biographic information triggers the creation of a notification message” which is composed by LENS and sent via NLETS “to the law enforcement agency for the state from which the alien is being released as well as the state in which the alien intends to reside (if they are not the same).”Footnote 52
Source: Cato.orgFootnote 53
EDDIE
EDDIE is a mobile app that ICE agents use during raids and interrogations to scan and upload fingerprints and photographs of a person to EID (before or without taking anyone into formal custody).Footnote 54
Using EDDIE, an ICE officer in the field can “immediately query other government databases to determine if they contain the same fingerprints as those collected by ICE.”Footnote 55 EDDIE can verify the identity of a subject presumably already known to ICE and is also used to identify a subject who is unknown to ICE by querying other government databases.
EDDIE can query the FBI’s NGI system for criminal history information and IDENT for a person’s immigration history. In response to the query, NGI and/or IDENT send a response, in less than a minute, to EDDIE indicating whether there is a fingerprint match. A response with a positive “hit” in IDENT includes a “hit level” (based on the presence or absence of derogatory information found in the databases). This information can be manually entered into EID. The NGI response includes a list of potential candidates who may match the prints submitted by EDDIE. NGI also provides the candidate’s Identity History Summary, which was formerly referred to as a “rap sheet.”
Information collected by EDDIE and uploaded to EID is viewable through EAGLE, allowing agents and officers in different locations to collaborate on a case. As a 2019 PIA described, “If an officer in the field enters data in EDDIE, another officer sitting at his or her workstation can view the information in EAGLE and enter additional data if needed. Likewise, an officer at his or her workstation can enter information in EAGLE, and an officer in the field can view it in EDDIE.”Footnote 55
8. Based on the above searches, ICE’s data analyst at LESC decides whether ICE has the basis to issue a detainer or arrest you.
The ACRIMe user prepares an Immigration Alien Response (IAR) that recommends to an ICE deportation officer whether you might be removable.Footnote 57 The IAR includes a person’s last known immigration or citizenship status, basic biographical information and criminal history. ACRIMe then electronically returns the IAR to both the requesting agency and the ICE ERO Field Office that is in the region of the requestor. If the analyst decides that a person might be deportable, then an ICE agent or officer can lodge a detainer via the ACRIMe system, and the IAR is routed to the local ICE field office which has jurisdiction.Footnote 58 Whatever the decision, an ICE field office can still carry out its own search, and has unchecked power to decide when the “evidence” it has is enough to justify a detainer or arrest.Footnote 59
9. The IAR is sent from LESC to an ICE field office, and/or PERC.
ACRIMe allows contract analysts at PERC to search multiple criminal legal, DHS and commercial databases to cross-check for any possibility of deportability. ICE field officers can access the analyst’s research via ACRIMe as well, and can also conduct their own research and investigation.
PERC is a newer center, established in January 2015.Footnote 60 ICE contract analysts at PERC attempt to identify, locate, and build a case against people whom it suspects are deportable. This includes people who have been previously ensnared by the automated data criminalization system, but were released before ICE picked them up. PERC creates detainers all day and night, scraping datasets that collect everything from social media posts to family members’ naturalization records to try to justify “probable cause” for a detainer.
An ongoing lawsuit, Gonzalez v. ICE, called into question whether issuing detainers based on incomplete and inaccurate databases violates the constitution, and enjoined several states, temporarily preventing them from honoring PERC detainers. However, a Ninth Circuit ruling in September 2020 overturned the prior injunction.Footnote 61
Additional databases consulted by PERC analysts may include: CLEAR and/or LexisNexis
CLEAR and/or LexisNexis
Among the other systems listed above, until February 2021, PERC used Thomson Reuters’ CLEAR.Footnote 62 CLEAR includes more than 400 million names, addresses and service records and is updated daily.Footnote 63 CLEAR’s contract expired in February, and it remains unclear if it will be renewed — in part due to pressure from Thomson Reuters shareholders. Unfortunately, there are always contractors waiting in the wings to fill the gaps, and LexisNexis signed a contract in April 2021 to provide similar services for ICE in April, apparently replacing CLEAR.Footnote 64
Data fed into commercial data aggregators come from numerous government and other commercial databases.Footnote 65 These include real-time incarceration records (including booking photos), cell phone location and automated license plate reader data history, utility information from Equifax, and social media accounts. Although PERC agents print detainers, they do not “investigate” beyond database checks.Footnote 66 A 2019 New York Times Magazine article detailed some of the ways that PERC works with ICE agents on the ground to stalk immigrants who are not in custody.Footnote 67
10. ICE uses ACRIMe to issue a detainer to the jail where you are held.
Your fate is in the hands of your jailers.
Best case scenario: Even if the cops do not honor ICE’s detainer, and you are released, your “permanent record” is now beefed up and freshly linked to criminalizing data. If you encounter law enforcement or immigration officials in the future, it will only take a quick database check for them to decide that you’re worth detaining and investigating further. Also, ICE could decide at any time to prioritize coming for you. They have very updated information about where to find you.
Worst case scenario: If the jail decides to hold you or notify ICE about the details of your release, ICE could send over an agent to arrest you. If things go badly, you could be deported within days.
- 1 a Immigrant Legal Resource Center, “Stop and Identify Statues in the United States,” February 1, 2018, https://www.ilrc.org/sites/default/files/resources/stop_identify_statut….
- 2 a “Who We Are,” Nlets website, accessed July 12, 2021, https://www.nlets.org/about/who-we-are.
- 3 a “Our Members,” Nlets website, accessed July 8, 2021, https://www.nlets.org/our-members/grantmaps?mapid=d26b4e70-934e-11e3-9a….
- 4 a National Immigration Law Center, “Backgrounder: Face Recognition and Driver's License Photo–Sharing,” October 1, 2019, https://www.nilc.org/issues/drivers-licenses/face-recognition-and-dl-ph….
- 5 a “Section 15: Criminal History Record Information Transactions (CHRI),” Nlets Wiki, accessed July 8, 2021, https://wiki.nlets.org/index.php/Section_15:_Criminal_History_Record_In….
- 6 a “Contract Opportunity: Nlets Award Details,” August 1, 2020, https://sam.gov/opp/a4e17cafd607410bbe741d610b48fa85/view#attachments-l….
- 7 a Julie Mao, State Driver’s License Data: Breaking Down Data Sharing and Recommendations for Data Privacy, Just Futures Law, March 2020,12, https://justfutureslaw.org/wp-content/uploads/2020/04/2020-3-5-State-DM….
- 8 a “Section 15: Criminal History Record Information Transactions (CHRI),” Nlets Wiki.
- 9 a “Next Generation Identification (NGI) Services,” https://www.fbi.gov/services/cjis/fingerprints-and-other-biometrics/ngi.
- 10 a NCIC, Operating Manual, undated, https://saccoprobation.saccounty.net/Documents/Miscellaneous/NCIC%20Ope…; see also Center for Constitutional Rights, “National Security Entry-Exit Registration System (NSEERS) Freedom of Information Act (FOIA) Request,” Center for Constitutional Rights, January 3, 2017, https://ccrjustice.org/home/what-we-do/our-cases/national-security-entr….
- 11 a Hannah Gladstein, et al., Blurring the Lines: A Profile of State and Local Police Enforcement of Immigration Law Using the National Crime Information Center Database, 2002-2004 (New York University School of Law: Migration Policy Institute, 2005). https://www.migrationpolicy.org/sites/default/files/publications/MPI_re…
- 12 a National Immigrant Justice Center, “Policy Brief: Disentangling Local Law Enforcement from Federal Immigration Enforcement,” January 13, 2021, https://immigrantjustice.org/research-items/policy-brief-disentangling-….
- 13 a The databases, identified in May 2019 court testimony in the Gonzalez v. ICE trial, include: IDENT, CIS, CLAIMS 3 and CLAIMS 4, ADIS, SEVIS, TECS, EOIR, EID, ENFORCE/EARM, SQ11, SQ94, ELIS 1 & 2, the California Birth Index, CCD, RAPS, and the NCIC and NLETS databases.
- 14 a Department of Homeland Security, “Privacy Impact Assessment for the Homeland Advanced Recognition Technology System (HART) Increment 1 PIA,” February 24, 2020, https://www.dhs.gov/sites/default/files/publications/privacy-pia-obim00….
- 15 a DHS, HART PIA, 7
- 16 a DHS, HART PIA.
- 17 a “DHS's Automated Biometric Identification System IDENT – the Heart of Biometric Visitor Identification in the USA,” Thales: Customer Cases, January 19, 2021, https://www.thalesgroup.com/en/markets/digital-identity-and-security/go….
- 18 a American Friends Service Committee, “Northrop Grumman Corp.,” Investigate, January 8, 2019, https://investigate.afsc.org/company/northrop-grumman.
- 19 a John Bowden, “DHS Moving Biometrics Database to Amazon Cloud,” TheHill, May 7, 2020, https://thehill.com/policy/technology/496624-dhs-moving-biometrics-data….
- 20 a Agencies submit IAQs to inquire about an individual’s citizenship and/or immigration status.
- 21 a U.S. Immigration and Customs Enforcement, “Enforcement and Removal Operations: LESC, PERC, and NCATC Fact Sheet,” May 11, 2020, https://www.ice.gov/doclib/about/offices/ero/pdf/todCenterOverviews.pdf.
- 22 a “Nlets Award Details,” SAM.gov.
- 23 a IAQs come to the ACRIMe Operations Module through the National Law Enforcement Telecommunications System (NLETS), which is a computer-controlled message-switching network that connects federal, state, local, and international agencies together for the purpose of information exchange.
- 24 a U.S. Department of Homeland Security, “Privacy Impact Assessment Update for the ACRIMe,” September 28, 2018, https://www.dhs.gov/sites/default/files/publications/privacy-pia-ice-ac….
- 25 a National Archives and Records Administration, “Request for Records Disposition Authority: Alien Criminal Response Information Management System (ACRIMe),” October 31, 2017, https://www.archives.gov/files/records-mgmt/rcs/schedules/departments/d….
- 26 a U.S. Department of Homeland Security, “Alien Criminal Response Information Management System (ACRIMe),” April 22, 2010, 4, https://www.dhs.gov/sites/default/files/publications/privacy-pia-ice-02….
- 27 a DHS, “ACRIMe,” 2.
- 28 a U.S. Department of Homeland Security, “DHS/USCIS/PIA-009 Central Index System,” https://www.dhs.gov/publication/dhsuscispia-009-central-index-system.
- 29 a U.S. Department of Homeland Security, “Privacy Impact Assessment for the Computer Linked Application Management System and Associated Systems (CLAIMS 3) DHS Reference No. DHS/USCIS/PIA-016(d),” June 30, 2020, https://www.dhs.gov/sites/default/files/publications/privacy-pia-uscis0….
- 30 a Gonzalez, 416 F. Supp. 3d at 1009.
- 31 a U.S. Department of Homeland Security, “Privacy Impact Assessment Update for the Computer Linked Application Information Management System DHS/USCIS/PIA-015(a),” August 31, 2011, https://www.dhs.gov/sites/default/files/publications/privacy_pia_uscis_….
- 32 a U.S. Department of Homeland Security, “Privacy Impact Assessment for the HART Increment 1 PIA,” February 24, 2020, https://www.dhs.gov/sites/default/files/publications/privacy-pia-obim00….
- 33 a U.S. Department of Homeland Security, “DHS/CBP/PIA–024 Arrival and Departure Information System,” December 21, 2020, https://www.dhs.gov/publication/arrival-and-departure-information-system.
- 34 a Gonzalez, 416 F. Supp. 3d at 1010.
- 35 a U.S. Department of Homeland Security, “Privacy Impact Assessment for the Student and Exchange Visitor Program (SEVP) DHS/ICE/PIA-001,” February 20, 2020, https://www.dhs.gov/sites/default/files/publications/privacy-pia-ice-se….
- 36 a U.S. Department of Homeland Security, “Privacy Impact Assessment Update for the ACRIMe,” September 28, 2018, 16, https://www.dhs.gov/sites/default/files/publications/privacy-pia-ice-ac….
- 37 a Gonzalez v. U.S. Immigr. & Customs Enf't, 975 F.3d 788, 821 (9th Cir. 2020).
- 38 a Gonzalez v. U.S. Immigr. & Customs Enf't, 416 F. Supp. 3d 995, 1008 (C.D. Cal. 2019), rev'd and vacated, 975 F.3d 788 (9th Cir. 2020).
- 39 a b Gonzalez, 416 F. Supp. 3d at 1008.
- 40 a Department of Homeland Security, “Chief Freedom of Information Act Officer Report,” March 2020, 5, https://www.dhs.gov/sites/default/files/publications/2020_dhs_chief_foi…
- 41 a Gonzalez, 416 F. Supp. 3d at 1012.
- 43 a Muñiz, “Bordering,” 1659.
- 44 a U.S. Immigration and Customs Enforcement, Comprehensive Plan for Immigration Data Improvement: Fiscal Year 2017 Report to Congress, 2018, 37, https://www.dhs.gov/sites/default/files/publications/ICE%20-%20Comprehe….
- 45 a EAGLE replaced ENFORCE Apprehension Booking Module (EABM) in 2012.
- 46 a U.S. Department of Homeland Security, “Privacy Impact Assessment Update for the Enforcement Integrated Database (EID) – EAGLE DHS/ICE/PIA-015(e),” July 25, 2012, 4, https://www.dhs.gov/sites/default/files/publications/PIA%20Update%2C%20….
- 47 a DHS, “PIA Update for the Enforcement Integrated Database (EID) – EAGLE DHS/ICE/PIA-015(e),” 2012.
- 48 a PACER is owned and maintained by the Administrative Offices of the US Courts.
- 49 a U.S. Department of Homeland Security, “Privacy Impact Assessment Update for the Enforcement Integrated Database (EID) Prosecutions Module (PM), Electronic Removal Management Portal (eRMP), Operations Management Module (OM²), Law Enforcement Notification System (LENS), and Compliance Assistance Reporting Terminal (CART) DHS/ICE/PIA-015(i),” December 3, 2018, https://www.dhs.gov/sites/default/files/publications/privacy-pia-ice-ei….
- 50 a U.S. Department of Homeland Security, “Privacy Impact Assessment Update for the Enforcement Integrated Database (EID) – EAGLE, EDDIE, and DAVID DHS/ICE/PIA-015(j),” May 14, 2019, https://www.dhs.gov/sites/default/files/publications/privacy-pia-ice-ei…, and U.S. Department of Homeland Security, “Privacy Impact Assessment Update for the Enforcement Integrated Database (EID) Law Enforcement Notification System (LENS) DHS/ICE/PIA-015(g),” September 22, 2015, https://www.dhs.gov/sites/default/files/publications/PIA%2C%20ICE-EID%2….
- 51 a Law enforcement agencies may include state identification bureaus, fusion centers, state and local law enforcement agencies, or some combination thereof, as determined by the state receiving the notification, according to the 2015 PIA for LENS.
- 52 a DHS, “PIA Update for the Enforcement Integrated Database (EID) Law Enforcement Notification System (LENS),” 2015, https://www.dhs.gov/sites/default/files/publications/PIA%2C%20ICE-EID%2….
- 53 a https://www.cato.org/sites/cato.org/files/2020-05/EXH%20221%20-%20Victo…
- 54 a U.S. Department of Homeland Security, “Privacy Impact Assessment Update for the Enforcement Integrated Database (EID),” May 20, 2011, https://www.dhs.gov/sites/default/files/publications/privacy-pia-ice-ei….
- 55 a b DHS, “PIA Update for the EID – EAGLE, EDDIE, and DAVID DHS/ICE/PIA-015(j),” 2019.
- 57 a According to the ACRIMe PIA from September 2018, “ICE has expanded the users of ACRIMe beyond the LESC to include ERO officers located at the Pacific Enforcement Response Center (PERC) as well as in ERO field offices and command centers across the country.” DHS, “PIA for ACRIMe,” September 28, 2018.
- 58 a DHS, “PIA for ACRIMe,” September 28, 2018, 2.
- 59 a By law, ICE must have a “reason to believe” someone is in violation of immigration law, 8 U.S.C. § 1357, and courts uniformly conclude that “reason to believe” is the same as “probable cause” for arrest. But there is no external check on ICE’s decision to arrest or issue a detainer, and there is no real consequence when ICE fails to follow this standard, so in practice, ICE can arrest people when it deems fit, on any basis it deems fit, as seen with the targeted arrests of anti-deportation activists in recent years.
- 60 a “Pacific Enforcement Response Center (PERC),” ICE website, accessed April 26, 2021, https://www.ice.gov/video/pacific-enforcement-response-center-perc.
- 61 a Gonzalez, 975 F.3d at 826.
- 62 a “CLEAR for Federal Government Investigations,” Government Investigations | CLEAR | Thomson Reuters, accessed April 26, 2021, https://legal.thomsonreuters.com/en/products/clear-investigation-softwa….
- 63 a Drew Harwell, “ICE Investigators Used a Private Utility Database Covering Millions to Pursue Immigration Violations,” Washington Post, February 26, 2021, https://www.washingtonpost.com/technology/2021/02/26/ice-private-utilit….
- 64 a Sam Biddle, “LexisNexis to Provide Giant Database of Personal Information to ICE,” The Intercept, April 2, 2021, https://theintercept.com/2021/04/02/ice-database-surveillance-lexisnexi….
- 65 a Dena Kozanas, U.S. Department of Homeland Security’s (DHS) 2019 Data Mining Report to Congress, December 2, 2020, 36, https://www.dhs.gov/sites/default/files/publications/2019_data_mining_r….
- 66 a Gonzalez, 975 F.3d at 799.
- 67 a Funk, “How ICE Picks Its Targets in the Surveillance Age.”